Text
[Wk10] Case Study: Emergency!
Emergencies are regular occurrences - you don’t know when or where they will strike, or what they will look like, but you know they will strike.
Managing the Response to a Mobile Mass Shooting - Police Foundation
Key Themes
- Build relationships (leader to leader and organisation to organisation) - during routine operations so that they are in place, when or if a critical incident occurs.
- Regional public safety partners should discuss, plan, and exercise coordinated responses to critical incidents including multi-agency command and control, tactical engagement, investigations, emergency communications, and the distribution of public information.
- Emergency communication policies, procedures and practices should ensure the timely and accurate intake of information from multiple public sources (e.g. voice, email, text, pictures, video) and transmission to all law enforcement personnel served by the system.
- Agencies should coordinate the release of information regarding incidents to the public, through a trained public information officer, using social media and other contemporary communication strategies, to send unified public safety messages throughout the event
- Law enforcement personnel should receive emergency medical and tactical emergency medical training and be equipped to render aid to severely injured victims and colleagues.
- Attend to first responder and affected agency personnel (including dispatchers) wellness and mental health before, during and after a mass casualty incident.
0 notes
Text
[Extra] Bhopal Investigation
Source: https://en.wikipedia.org/wiki/Bhopal_disaster
- Also known as the Bhopal gas tragedy, was a gas leak incident in December 1984
- World’s worst industrial disaster -> over 500 000 people were exposed to methyl isocyanate (MIC) gas
- Immediate death toll = 2 259, rose to 3 787
Causes
Two main lines of argument:
- Corporate negligence: combination of under-maintained and decaying facilities, a weak attitude toward safety, culminating in worker actions that inadvertently enabled water the penetrate the tanks in the absence of properly working safeguards
- Worker sabotage: argues that it was not physically possible for the water to enter the tank without concerted human effort. That extensive testimony and engineering analysis leads to a conclusion that water entered the tank when a rogue individual employee hooked a water hose directly to an empty valve on the side of the tank.
This water entry route could not be reproduced despite strenuous efforts by motivated parties. UCC claims that a “disgruntled worker” deliberately connecting a hose to a pressure gauge connection was the real cause.
Corporate Negligence
- Management (some extent, local government) underinvested in safety, which allowed for a dangerous working environment to develop
- Filling of the MIC tanks beyond recommended levels, poor maintenance after the plant ceased MIC production in 1984 -> several safety systems to be inoperable due to poor maintenance, and switching off safety systems to save money (including the MIC tank refrigeration system which could have mitigated the severity of the disaster)
- Undersized safety devices and the dependence on manual operations
- Lack of skilled operators, reduction of safety management, insufficient maintenance and inadequate emergency action plans
Underinvestment
- Attempts to reduce expenses, $1.25 million of cuts were placed upon the plant
- Promotions were halted, seriously affecting employee morale
- Workers were forced to use English manuals, even though only a few had a grasp of the language
- Only 6 of the 12 operators were still working with MIC and the number of supervisory personnel had also been halved
- No maintenance supervisor was placed on the night shift and instrument readings were taken every 2 hours instead of every hour
- 70% of the plant’s employees were fined before the disaster for refusing to deviate from the proper safety regulations under pressure from the management
Adequacy of Equipment and Regulations
- Not well equipped to handle the gas created the sudden addition of water to the MIC tank
- MIC tank alarms had not been working for 4 years and there was only one manual back-up system
- The flare tower and several vent gas scrubbers had been out of service for five months before the disaster
- Even the steam boiler, intended to clean the pipes, were not operational for unknown reasons
- Slip-blind platers were not installed and their installation had been omitted from the cleaning checklist
- As MIC is water-soluble, deluge guns were in place to contain escaping gases from the stack -> the water pressure was to weak to spray high enough
- The MIC tank pressure gauge had been malfunctioning for roughly a week
- No action plans had been established to cope with incidents of this magnitude
Safety Audits
- Senior officials were aware of - 61 hazards, 30 of them major and 11 minor in the dangerous phosgene/methyl isocyanate units
- Worker performance was below standards
- Sept 1984 Audit warned “a runaway reaction could occur in the MIC until storage tanks, and that the planned response would not be timely or effective enough to prevent catastrophic failure of the tanks.”
Impossibility of the “Negligence”
- Water from work nearby was diverted due to combination of improper maintenance, leaking and clogging, and eventually ended up in the MIC storage tank.
- Not possible because:
1. The pipes were only 1/2 inch and were physically incapable of producing enough hydraulic pressure to raise the water more than the 10 feet necessary to enable “back flow” into the MIC tank
2. A key intermediate value would have had to be open for the Negligence argument to apply. Marked “tagged” closed, meaning that it had been inspected and found to be closed.
3. Would have had to flow through a significant network of pipes ranging from 6 to 8 inches in diameter, before rising ten feet. Water would have remained in the pipes but Indian government investigations revealed the pipes were bone dry.
Employee Sabotage
- Claims that the incident was the result of sabotage, stating that sufficient safety systems were in place and operative to prevent the intrusion of water
- Likely that a single employee secretly and deliberately introduced a large amount of water into the MIC tank by removing a meter and connecting a water hose directly to the tank through the metering port
- UCC claims the plant stand falsified numerous records to distance themselves from the incident and absolve themselves of blame
- The evidence in favour of this point of view includes:
1. A key witness that testified the control room as “tense and quiet”
2. Another witness, noticed that the local pressure indicator on the critical Tank 610 was missing and that he had found a hose lying next to the empty manhead
3. Testimony was corroborated by other witnesses
4. Graphological analysis revealed major attempts to alter log files and destroy log evidence
5. Other log files show that the control team and attempted to purge 1 ton of material out of Tank 610 immediately prior to the disaster. An attempt was then made to cover up this transfer via log alteration.
6. A third witness was told that water had entered through a tube that had been connected to the tank
7. A fourth key witness stated that after the release, two MIC operators had told him that water had entered the tank through a pressure gauge.
0 notes
Text
[Wk8] Tutorial
Fallback Attack -> HTCPS -> RESEARCH!
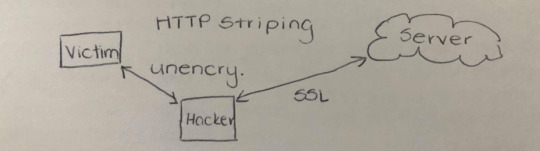
Latent errors - multiple protection, so one thing fails but don’t realise until another thing breaks and so on. -> Find examples in computer security
Block Cipher Modes
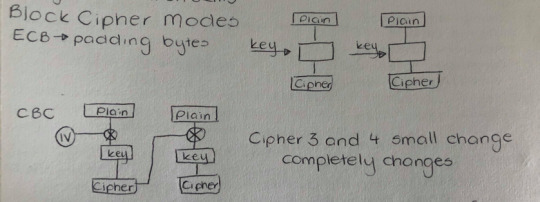
CTR length increase by one and everything after the change completely changes
Web CTF - plsdnonthaq.me
Case Study: Ghost
- Very similar to Houdini
- Common shared secret
0 notes
Text
[Extra] Data Breach Prediction
I hypothesis that over the next twelve months there will be a major breach of one of the big four banks. Based on the current ransomware being utilised in the US.
0 notes
Text
[Wk8] Case Study: Ghost
Courtesy of SteffenJohansen’s 2016 Blog Post
“The Stargate problem is the scenario when you have a group of military people standing outside a Stargate to another dimension/reality/universe/whatever (irrelevant). One of the brave round cadets volunteers to walk through the portal and ends up in this fantastic universe, full of beautiful, charismatic aliens. One of the aliens asks if he can join the cadet back into his universe. The cadet agrees. When they walk back into the Earth universe, the cadet disintegrates and becomes a ghost. The alien can however see and hear the ghost, but no living thing on Earth can either see or hear the ghost of the young cadet. How can one ensure that the ghost can communicate legitimately through the alien, with the people of Earth?”
Q. What would you M do to get from X his report on the Alien’s (A’s) planet?
- Utilise a common shared secret (hard to know the technology capabilities or the aliens or what information they could have received)
0 notes
Text
[Extra] Buffer Overflow Challenges
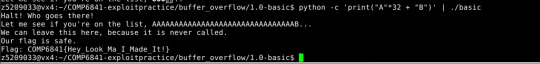
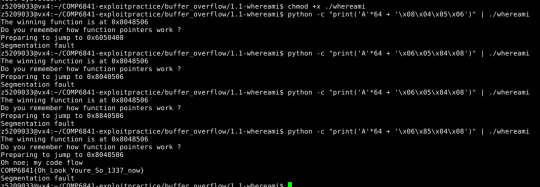
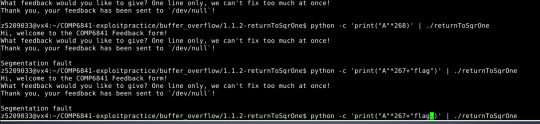
For the last challenge I was able to find where the segmentation fault was but was not sure what to do next.
0 notes
Text
[Wk8] Activities
Google Yourself
I downloaded my Facebook data. some of the types of data I found where:
- About You
- Comments - every comment I have ever made on ever post regardless of my or others privacy settings
- Events
- Files
- Following and Followers
- Friends
- Groups
- Likes and Reactions - every like and reaction I have ever made
- Location - surprisingly this file was empty
- Marketplace
- Messages...
One of the most surprising things I discovered was conversations and messages that I though had been deleted actually had not. Which is super scary that they store every piece of data you have “deleted”.
Spot the Fake
The Shed at Dulwich Hill
Created London’s highest rate restaurant - without the restaurant ever existing in the first place.
Banksy Fake Currency
The British artist create $1M of fake currency depicting Princess Diana in the place of Queen Elizabeth. His original plan was to throw the fake currency off the top of a building as an act of satire, but quickly changed plans after visiting a venue with a few of the fakes and realised no one had noticed.
Dropbears
The Australian Museum has posted a section on their website describing The Australian Drop bear as non-fatal to humans despite persisting myths of human attacks.
Gates of Heaven



The Gates of Heaven has become a viral photo travel destination due to its incomparable beauty. However the stunning “glass lake” is only an illusion created using a piece of mirror under the camera lens. It could be detected my doing further research into this tourist destination and prevented through media coverage highlighting the hoax.
Something that could be easily faked...
Membership to the UNSW gym. The Gym has really slack security and you can easily borrow one of your friends ID cards that have a membership to get in.
Authentication
Time-Based One-Time Password
TOTP is an extension of the HMAC-based One-Time Password Algorithm (HOTP) generating a one-time password by utilising the uniqueness of the current time. Because of the latency, both network and human, and unsynchronised clocks, the one-time password must validate over a range of times between the authenticator and the authenticated.
Weaknesses and Vulnerabilities:
- TOTP can be phished -> require attackers to proxy the credentials in real time rather than collect them later on in time
- Implementations that don’t limit login attempts are vulnerable to brute forcing of values
- An attacker who steals the shared secret can generate new, valid TOPT values at will.
- TOTP values are valid for longer than the amount of time they show on the screen (generally twice as long)
Practical Considerations:
- For subsequent authentications to work, the clocks of the authenticated and the the authenticator need to be roughly synchronised (the authenticator will typically accept one-time passwords generated from time stamps that differ by +/-1 time interval from the authenticated’s timestamp.
Login Leaks
My attempt at the manual login leaks...

0 notes
Text
[Wk8] Lectures
Topic - Human Error, Mistakes, Accidents and Disasters
Security Theatre:
- This week = Fog of War
- Next week = The China syndrome -> EXAM film
When something goes wrong, what is the root cause?
- Root cause analysis
1. User error (human error) -> hero & villain
2. Culture
3. ? -> the actual cause
- “Last touch” -> blame the person who last touched it. The last person through the door -> puppy analogy
HUMAN WEAKNESS:
- Honesty -> Commander in Cheat & University Honour Code
- Mis-direction and limited focus and Chekhov 1
-> limited focus, social engineers and magicians utilise this
- Frequency gambling - “what has worked in the past will work in the future”
- Availability heuristic - Kahneman 3
“Habit diminishes the conscious attention with which our actions are performed” - William James 1980
- His obsession: “those factors which lead to and sustain wishful thinking rather than wise thinking”
- Satisficing and bounded rationality
- People prefer positive statements
- Marshmallow analogy - “forget about the marshmallow” only tests at the end - toy train analogy
- Overriding technology to verify generalisations rather than falsify them -> “The human understanding when it has once adopted an opinion draws all things else to support and agree with it” - Francis Bacon 1620
- Confirmation bias - orientation analogy
- Cognitive strain
- Group-think syndrome -> what you value more than anything is to belong in a group rather than challenge things
- Developmental phases:
1. Procedural
2. Meta-procedural
3. Conceptual
- Redundancy = common mode failure
- Common mode failure = one thing cause another thing to fail
SYSTEMS
Cassandra and Apollo and hindsight and Chekhov and simplification
- Cassandra and Apollo -> always see the future (gift) she burned him so he tainted the gift... “no one will ever believe you”
- Hindsight
- Chekhov Gun -> if there is something noticeable then it is going to be used
-> belief event has only one significant cause
-> plan for fewer contingencies than occur
-> ability to control outcomes -> the illusion of control
-> hindsight bias = knowledge of outcome of previous event increases perceived likelihood of that outcome
- Complexity coherence coupling visibility 5
- Defense in depth
- Operator deskilling due to Automatic safety devices
- Common mode failures
- Latent vs active failures
- Kings Cross and Herald for free enterprise 6
- Normal accidents
1. a story (made up)
2. a story (real)
“Dead Battles like dead generals hold the military mind in their dead grip, and Germans, no less than other peoples prepare for the last war.” - Barbara Tuchmann
JUST CULTURE:
Research one of the following:
- Chernobyl
- Bhopal
- Challenger
Privacy
-> right to be free of undue surveillance
Methods of surveillance:
- Lighter method
- Incognito mode -> stops cookies - not very effective
- Privacy focused browsers -> Duck Duck Go
- Take care of your accounts -> log out when you can, don’t sign up with
other accounts and LIE!
- Heavier method:
- VPN (https://openvpn.net) -> have to trust the VPN provider - based on
whether or not they store data logs
- Onion Routing (3 layers)
- Problems:
- Using it and then logging into a website violating client-server anonymity
- Timing attack
“Equivalent to saying you don’t care about free speech because you have nothing to say” - Edward Snowden
- Express VPN - google “where am I” incognito
Should I be concerned? -> Imbalance of Power
Digital Forensics
- Branch of forensic science
- Stages:
1. Acquisition/imaging
2. Analysis
3. Reporting
- Types:
- Computer Forensic
- Mobile Device
- Network Forensics
- Database Forensics
- Video/Audio Forensics
- Tooling:
- enCase
- Autopsy
- Drives and portioning (FAT32) -> https://...
- WriteBlocker to stop the disk from being changed
- Hash it so you can know if it has been changed
Afternoon Lecture
Normal Accidents - Three Mile Island
-> imagine, new complex technology not a nuclear reactor
-> numerous things that went wrong
Normal accident = a system will undoubtedly fail -> when they do go wrong make sure that the impact will be minimised
UNSW Breach Advice:
1. Determine most important assets and protect those
2. Assume you are going to be breached but set it up so the damage will be minimised
-> prepare 2 different media releases
-> don’t hold on to valuable data
0 notes
Text
[SA5.4] Something Awesome Reflection
Final Reflection
Overall, I am very proud of my analysis of the impact of the Assistance and Access Act on the interests of Australian citizens. I am also really happen with my submission to the Parliamentary Joint Committee on Intelligence and Security however I am disappointed that I am unable to submit it. I had every intention of submitting my concerns anonymously but unfortunately this is not an option. In order to produce a submission you have to create a MyParliament Account, I tried to create an account using an alias but never received the confirmation email. Even if I was able to create a profile the submission to the PJCIS had already closed and they were only open for a short period of time.

0 notes
Text
[SA5.3] Something Awesome Reflection
Progress Three
I fixed my critical analysis of the Assistance and Access Act concluding that the introduction of the Act was a step in the right direction but was poorly execute, in order for it be effective in protecting the interests of Australian citizens, it must undergo extensive changes. I highlighted some of the changes that should be made in my submission, namely:
- Simply the definition of “designated communication providers”
- Permanently restrict the legislation from being able to apply to other agencies or private organisations
- Stop international access to collected data, limiting international interference and pressures
- Create a separation of powers between the judicial, legislative and executive branches of Government
- Create transparency by increasing the scope of information that can be revealed without compromising national security
- Review the economic impact of the legislation on The Australian technology industry and Australian economy
- Emphasise that the Parliamentary Joint Committee on Intelligence and Security needs to focus on protecting the interests of the Australian people not the current Government
0 notes
Text
[SA5.2] Something Awesome Reflection
Progress Two
Utilising my summary notes and blog posts, I created a first draft of my report. In my analysis of the Assistance and Access Act, I focused on:
- The Ambiguity of the Act
- Influence of International Pressures
- Inadequate Judicial Oversight
- Lack of Transparency
- Expedited Nature of Legislation
- Impact of Australian Technology Industry
Going through editing my draft, I notice that it was more explanatory rather than analytic which I will have to remedy.
0 notes
Text
[SA5.1] Something Awesome Reflection
Progress One
Finished gathering resources to help with my analysis and submission. I collated a variety of different resources particularly government sources including legislation, Department of Home Affairs, media releases and statements from the Parliamentary Joint Committee on Intelligence and Security. I also gathered other resources in order to view effectively determine the impact of the Assistance and Access Act on the interests of Australian citizens, especially focusing on their digital rights.
0 notes
Text
[SA5.0] Something Awesome Reflections
Initial Goals
Derived from my something awesome proposal the initial goals of my assignment are to:
- Extensive research
- Demonstrate an in-depth understanding of the legislation
- Critically analyses the legislation in relation to how effectively they protect the interests of Australian citizens
- Drafts a logical and coherent submission
- Send the submission to the appropriate government body
0 notes
Text
[SA4.1] Something Awesome Powerpoint
Here is the link to the Powerpoint, I used for my Something Awesome Video and will use in my presentation on Thursday:
https://drive.google.com/open?id=1Mj9wvJB2qwv6mGFzAFlHjhaomwMgmvu1
0 notes
Text
[SA4.0] Something Awesome Video
I made my video using Microsoft Powerpoint, its is only 3 minutes long but somehow in the download it add 6 seconds. I uploaded into to YouTube have have embedded a link. I will be presenting in class on Thursday as well.
youtube
0 notes
Text
[SA3.0] Something Awesome Submission
The following is the link to my submission regarding the Telecommunications and Other Legislation (Assistance and Access) Act 2018 to the government.
https://drive.google.com/open?id=1PfIo5YegUXV_xylPNTXPqN3M7C7DFG4q
Unfortunately, I was unable to submit my concerns due to a number of reasons:
1. Inability to be anonymous
In order to submit concerns about the legislation you had to create a MyParliament account. Considering I am directly conveying my opinions to the Government I wanted to do this anonymously. I set up a fake persona with an email account and tried to set up an account but the confirmation email never came through.
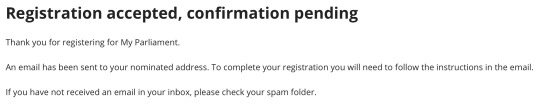
2. Closed Submissions
The submissions to the Parliamentary Joint Committee on Intelligence and Security were only open for a very short period of time and unfortunately I missed the window.
0 notes
Text
[SA2.0] Something Awesome Essay
This is the link to my completed essay on the topic of Critically Analyse the Impact of the Telecommunications and Other Legislation (Assistance and Access) Act 2018. I am really happy with the finished product, it took longer to complete than intended but it is in-depth and reflective.
https://drive.google.com/open?id=1vFuREtePNC1mxMg7gliwjRORlbJlohKv
I have finished my submission that corresponds with my report, I just need to edit it.

1 note
·
View note