Text
Add AWS CLI to Windows Terminal
I am a fan of Windows Terminal and some of the recent things Microsoft seem to be doing for SysAdmins. I like having all the tools I need in a single spot. Adding the AWS CLI is fairly straight forward but makes life a heap easier. Start by installing Python from python.org if you don’t already have it on your machine. Once installed (take note of the version, which as of publishing is 3.11)…
View On WordPress
0 notes
Text
Hide the Bing button in Edge
I’m not a fan of the Bing button that now appears in Edge. Microsoft seem to have rushed it out as there isn’t an easy way to remove it. We’ll do this via a registry key (that can also be deployed via Group Policy)
Close out of Microsoft Edge completely and open the Registry Editor and navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft. Right-click on the Microsoft folder and select New >…
View On WordPress
0 notes
Text
Adopt Unifi Access Point over Internet or VPN using SSH
Adopt Unifi Access Point over Internet or VPN using SSH
If you’ve shipped some Ubiquiti Unifi Wireless access points to a remote site before adopting them or happen to have your controller on another network, you can log into them via SSH and point them to your Unifi controller. It performs discovery via basic L2 broadcast and DNS resolution of hostname unifi, if either of these methods do not reach a controller then you can follow these steps.
Get…
View On WordPress
0 notes
Text
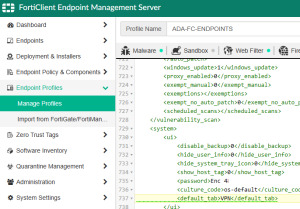
Set a Default Tab for FortiClient EMS
Set a Default Tab for FortiClient EMS
It’s been a while, but I am working on deploying an updated version of FortiClient for and company which is managed via EMS and InTune. One thing that bugs me (and many) is by default, the client UI will load into the Zero Trust Telemetry tab and the option to change the Default tab will be greyed out for the end user when managed. There is no UI setting in EMS but you can easily set the Default…
View On WordPress
0 notes
Text
Fixing Maximum connections reached by Clearing Connected Sessions on an APC UPS
Fixing Maximum connections reached by Clearing Connected Sessions on an APC UPS
I was trying to log into an APC UPS with the correct login but still received an error, The maximum number of web connections has been reached or simply Maximum connections reached. Knowing I had the right login credentials, and that no one else was logged into, I was a little perplexed. There is a straight forward fix but can be a little annoying.
Open up your favorite SSH client and connect…
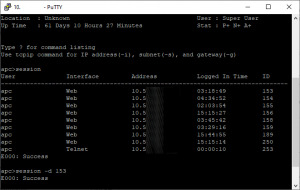
View On WordPress
0 notes
Text
Automate Lets Encrypt Renewals using Certify the web on Windows with Atlassian Jira behind a Apache Reverse Proxy
Automate Lets Encrypt Renewals using Certify the web on Windows with Atlassian Jira behind a Apache Reverse Proxy
So been a while since my last post. I’ve been recently pushing our machines into Azure as well as automating as much as possible. We’ve got an internal Jira instance that we use. It is still running totally on a VM with no fancy Azure PaaS features on it.
I have a Lets Encrypt SSL certificate managed using Certify the Web. I am running the free and awesome Community Edition and have added a…
View On WordPress
0 notes
Text
Queries for troubleshooting the Database Mail (dbmail) function of Microsoft SQL Server
Queries for troubleshooting the Database Mail (dbmail) function of Microsoft SQL Server
So just a quick one today. I was recently working on a SQL Server, running through some Database Mail setup and testing (see Microsoft Docs) with one of our applications. I needed a way to see what e-mails were being sent out as well as what wasn’t. The below queries will give you the info I was after, the first one shows any items that have run through DB Mail and their details for the last…
View On WordPress
0 notes
Photo
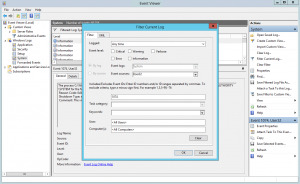
Get the last Reboot or Shutdown reason and user from the Windows Event Log Start by going into Event Viewer (Windows+R or the Start Menu and type eventvwr.msc). Navigate to the System Log under Windows, we then want to use Filter Current Log to allow us to only show Events with certain attributes (such as Source or IDs).
0 notes
Text
So getting BitLocker enabled in an Active Directory environment is fairly painless and helps to get your end user devices more Secure. I’ll outline the steps you need to take to enable it as well as get the recovery keys stored in Active Directory. I’ll also dive into replicating this setup on Azure AD/Intune in a future post.
First thing is to create a new GPO (i.e. Configure – BitLocker) – Edit it and navigate to Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption. Enable the following Options:
Choose drive encryption method and cipher strength (Windows 10 Version 1511 and later)
Choose drive encryption method and cipher strength (Server 2012, Win 8.1 etc…)
Choose how users can recover BitLocker protected drives
Store BitLocker recovery information in Active Directory Domain Services
Then go down one folder into Operating System Drives and enable the following:
Choose how BitLocker protected operationg system drives can be recovered
Once you’ve set this all up, it should look something similar to the image below.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Group Policy Settings for BitLocker
BitLocker Recovery Key in Active Directory
Now target the GPO to some machines and if you’re running 1809 (from what I’ve discovered so far) or later you’ll notice them start the BitLocker process to encrypt automatically. If not then you may need to check and ensure the TPM is enabled for the device (as we haven’t specified to encrypt devices without a TPM in this case).
What happens if you have already enabled BitLocker but now want to store the recovery keys in Active Directory? With this GPO set it will allow windows to write the recovery key to AD however we need to use the manage-bde utility, that is a command based utility that can be used to configure BitLocker
manage-bde -protectors -get c: for /f "skip=4 tokens=2 delims=:" %%g in ('"manage-bde -protectors -get c:"') do set MyKey=%%g echo %MyKey% manage-bde -protectors -adbackup c: -id%MyKey%
I saved that as a batch file and ran that on the machines that had already been encrypted prior to rolling out the GPO. Once run, it escrows the key into Active Directory.
The last bit you will need to do so you can actually see the keys in the Properties tab or via the Search function in Active Directory Users and Computers, ensure that the BitLocker RSAT is enabled in Server Features and Roles.
Enabling BitLocker with Group Policy and backing up Existing BitLocker recovery keys to Active Directory So getting BitLocker enabled in an Active Directory environment is fairly painless and helps to get your end user devices more Secure.
0 notes
Text
We’ve started to deploy the latest release of Windows 10 and it’s interesting to note that Microsoft have released with little fan-fare some changes to the way Updates are deployed for the 1903 release.
Microsoft are now pushing updates through what is called the Unified Update Platform (see this RPC Mag article). Anyway, the main thing is there is now a new product category for WSUS and Config Manager that needs to be configured before your clients will being to receive updates.
You’ll see there is now a Windows 10, version 1903 and later product – make sure that is ticked on your Update Management Tool for updates to by synchronised. Once we had that ticked, for Config Manager you may need to tweak your Automatic Deployment Rule to include additional filters based on how you have it setup. Microsoft have also blogged about these changes here.
Windows 10 May 2019 or 1903 Software Update Management Changes for WSUS and Config Manager We've started to deploy the latest release of Windows 10 and it's interesting to note that Microsoft have released with little fan-fare some changes to the way Updates are deployed for the 1903 release.
0 notes
Text
Copying files from one server to another as a different user (two separate domains) using PowerShell
Copying files from one server to another as a different user (two separate domains) using PowerShell
I’ve been working on needed to copy a number of files from one client site to another, my issue is that they have separate Active Directory domains and there is no trust between them. Using PowerShell, we can save a user credential and then use that to map a network drive with them and perform our copy.
We will setup the credential to be stored in a text file, although a cool feature of…
View On WordPress
0 notes
Text
Moving the SQL Server tempdb file location after SQL Server is installed
Moving the SQL Server tempdb file location after SQL Server is installed
Working with one of my education customers I recently had to perform some maintenance on their SQL Database server as they were running low on disk space AND had a free unused virtual disk where we could throw their tempdb onto (it was meant to go here but they didn’t place it there during installation). So I had the task of moving it over.
First step is to get an as-is of where tempdb currently…
View On WordPress
0 notes
Text
Deploy Firefox in the Enterprise with uBlock Origin, HTTPS Everywhere and Privacy Badger using Group Policy
Deploy Firefox in the Enterprise with uBlock Origin, HTTPS Everywhere and Privacy Badger using Group Policy
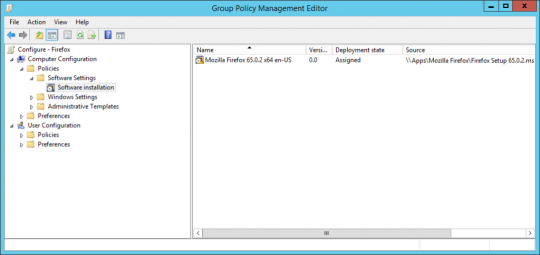
So we’ve been deploying Firefox for quite a while pretty much everywhere we can however, only recently have we started standardising the deployments across the organisation’s that we manage. We’ve deployed Internal Root CAs using the CCK2 method to improve our user experience with Deep Packet SSL inspection however setting up configurations and extensions and having that consistent was a…
View On WordPress
0 notes
Text
Change Windows 10 Taskbar Icons Script Deploying a custom taskbar for Windows 10
Change Windows 10 Taskbar Icons Script Deploying a custom taskbar for Windows 10
Over the summer holiday period, I was assisting a school with building out an SoE for the new year. One of the things we used to do with Windows 7 was tweak the Taskbar to contain only items we were after instead of the default items of Internet Explorer, Windows Explorer and Windows Media Player. To do this we implemented a VB Script that would make the changes on the fly. And since that…
View On WordPress
0 notes
Text
Using Stunnel to Allow Legacy Apps and Devices that do not support SSL POP3 or TLS SMTP to Connect to Office 365
Using Stunnel to Allow Legacy Apps and Devices that do not support SSL POP3 or TLS SMTP to Connect to Office 365
I’ve been busy lately assisting with a number of Office 365 migrations. Every single one is different and while many are straightforward, In some cases, you will find applications or devices that don’t support the requirements for connecting to Office 365 using TLS or SSL or they may not even work over standard ports such as 587. Working with one SMB recently, they had a critical Line of Business…
View On WordPress
2 notes
·
View notes