Text
Post-3: Individual Report(MAKING WEB CULTURES &15 March 2020)
Post-3: Assess how a social media platform is attempting to prevent online harassment
1. Introduction
With the advent of the Internet age, the delivery of information and communication content is more dependent on the network media. In the daily life of young people, Instagram, Facebook, Twitter, LinkedIn, Myspace, etc. are the most indispensable social software to contact friends and post mood changes. The social network has become an important platform for people to spread information and conduct social communication activities on the Internet. It is interactive, open, timely, and shared. The Pew Research Center in the United States recently released a new research report saying that 72% of adolescents use Instagram as a social platform, and that monthly active user has reached 1 billion (Lindsay et al., 2016). With more and more users communicating and disseminating information through social networks, security issues are becoming increasingly prominent, and it becomes easier to collect and use user privacy information through social networks; the risk of users 'privacy exposure is increasing and users' rights and interests The possibility of damage is also increasing. However, the problem of online harassment has also become increasingly prominent. In anonymous networks, many netizens have unscrupulously made malicious remarks, which has become a hidden danger that bothers netizens and threatens social security. Online harassment defines online harassment as offensive to others' names, purposeful embarrassment, entanglement, personal Threats, continued harassment and sexual harassment (Duggan, 2017). The thesis is based on the analysis of social media platforms leaking user privacy information and online harassment. How should media platforms consider and solve the online harassment problem? What steps to take to prevent online harassment.
2. Methodology
With the development of the real-name system of social platforms, more and more platforms require registrants to submit real personal information. For example, to find more friends on social platforms, users must provide more detailed personal information, such as education background, geographic location information, personal hobbies and other information. By analyzing these real data, the system can help you find more friends and get more interesting information. In this case, users are often in a dilemma. If all the real information is filled in, the user's privacy will be exposed on the network. But if you fill in false information, you cannot combine social networks with real life. In the process, many people are willing to use geographic sharing services to expose their activity trajectory on the Internet. Secondly, in addition to text information, users are also posting pictures and video information on the Internet. Through sharing content, social platforms can infer users' consumption trends, work conditions and a lot of information related to personal privacy. In this case, social networks also expose our relationships. Internet harassment. This article uses research methods in communication science. In this article, the survey method and content analysis method are specifically used to analyze the problem of online harassment. Through the analysis of existing online harassment surveys, the analysis results are reflected in numbers to reveal the nature and trends of these objects (Duriau et al., 2007).
3. Discussion about online harassment
With the rapid development of social networks, social networks have mastered a large amount of user information, and the security of the social network itself is of great significance to the privacy and security of users. There are two main types of privacy leaks on social media platforms. One is the leakage of user privacy by social networks for certain technical reasons, such as the existence of security holes in social networking sites, which has resulted in user information leakage due to hacking.
After the privacy breach, the most ironic consequence of the drama was the occurrence of cyber harassment. For the most part, social media is the most commonplace for online harassment. When asked where their recent experience of online harassment occurred, nearly 60% appeared on social networks (58%), saying it happened on social media. Similarly, in the Pew Research Center's 2014 survey of online harassment, most people thought that the harassment suffered by media and social platforms was their most recent (Duggan, 2017). The important signs of online harassment are harm and cause reasonable psychological fear. The investigation results show that online harassment is related to the violence of intimate partners. Depression and anxiety among those harassed by a partner (Lindsay et al., 2020). Many people have experienced online harassment, but for young people, harassment is a particularly common fact in online life. The study found that 8.6% to 52% of college students have experienced cyberbullying (Dilmaç & Aydoğan, 2009; Schenk & Fremouw, 2012), while 3.7% to 40% of college students have experienced online tracking. However, a replication research study on online harassment found that the number of victims among college students has almost tripled (from 15% to 43%) over the past decade (Lindsay & Krysik, 2012). Previous research has found that college students who suffer from cyberbullying are more likely to experience suicidal thoughts, sadness, depression, and difficulty concentrating than college students who do not suffer from cyberbullying (Schenk & Fremouw, 2012). There is no doubt that they have been subjected to some form of online harassment. Regarding the situation of online harassment, according to the sampling survey method in communication science, it attempts to indirectly understand the psychological activities of some respondents through various channels. Several different online harassment measures were used in some online harassment surveys in 2017, and the data showed that 45% of men and 39% of women experienced some form of online harassment but women between the ages of 18 and 34 say they are twice as likely to be sexually harassed online than men in that age range (20% vs. 9%) (Anderson and A. Vogels, 2020). For women of all ages, the consequences of online harassment are also more severe than for men.
In the survey, we found that nearly half of Americans aged 18 to 29 said they were called offensive names online (46%), and more than a third said that someone tried to embarrass them on purpose (37%). In addition to these acts, the notable share of young people has been subjected to more severe abuses. One in four (25%) people are personally threatened online, while a smaller but still noteworthy proportion is sexually harassed (15%), persistently harassed (16%) or stalked (13%). All in all, about two-thirds of young people (67%) have experienced some type of online harassment-41% experienced severe forms of harassment (Duggan, 2017).
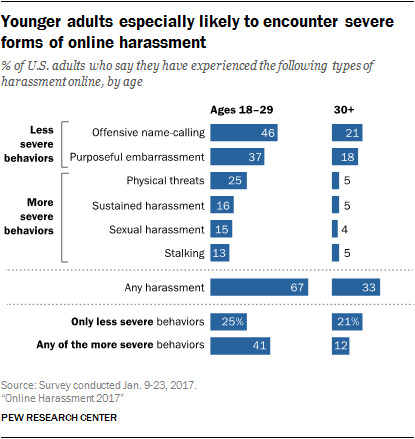
Using the content analysis method and comparative research method based on the survey information, we can analyze the problem of cyber harassment in the era of so-developed media, whether it is gender or ethnicity. At the same time, we also find that women are more harassed by cyber Severe and widespread and this may not be occupational, the survey found high levels of online harassment by female faculty and staff (22% have been harassed in the past year, compared with 6% for men). Most of the harassment reported by these women were committed by students or colleagues and occurred via email course-related websites or social media (Veletsianos, Houlden and Hodson, 2020).
4. Prevent online harassment measures
At present, more and more people realize that the privacy control problem of social the network is a key point that needs to be valued and resolved. To solve the privacy and security issues of users to solve the problem of online harassment of users, it is necessary to restore the user ’s psychology and behaviour There are several approaches to preventive measures taken by media social platforms.
4.1 Enhance users' awareness of information security
At present, the privacy and security issues of social networks have attracted the attention of many people but still, a large number of users ignore the security control of personal privacy while enjoying and sharing the fun on social networks. First of all, social media platforms can establish a credit system for users. Credits will be deducted if users send text or pictures that disclose personal privacy-related information, and sensitive words will be reminded and posted on social platforms when chatting with others Credit points will be deducted after the warning, such as gender, race and other sensitive words. Credit points will be banned if they are reduced to a certain level. Through such a credit system, it is conducive to improving the user's awareness of information security and also improving the level of civilized use of the platform by users, which will reduce the probability of network harassment to a certain extent. When using social networking sites, users will realize that if they want to continue to use the social media platform, they must abide by the rules of the platform, otherwise, they will lose the right to use it. Secondly, media platforms should strengthen the promotion of safe and healthy information, actively guide users, and on the premise of helping users understand and protect their privacy and social safety, it is very important to strengthen the platform itself to reject online harassment.
4.2 Technical support of the platform
For social networks, on the one hand, social networking websites should strengthen their security. The website takes reasonable and effective control measures to protect user privacy and sets rules to reduce the probability of abnormal use by users which greatly reduces network harassment possibility. On the other hand, social media platforms should raise the technical threshold and speed up technological innovation. Sensitive words and sensitive picture systems involving network harassment in the social process should be automatically identified and blocked to minimize the occurrence of network harassment.
5. Conclusion
Nowadays, the popularity of social networks provides users with many platforms. However, while providing users with communication and platforms, if they cannot protect the personal privacy and social processes that are related to the vital interests of users, this will cause serious problems for users. loss. Through research, we can find that the situation of online harassment will be affected by many factors. It may be gender and race and the situation of female harassment may be more serious. Then the protection measures for women on social platforms are more important. The media platform should improve the technical support of the platform itself and strengthen the user's awareness of security protection. Create a safe and reliable environment for social platforms to increase users' trust in the platform. Achieve the rejection of online harassment at the source.
6. Reference
1. Anderson, M. and Vogels, E. A. (2020). Young Women Often Face Sexual Harassment
Online – Including On Dating Sites And Apps. [online] Pew Research Center. Available
at: <https://www.pewresearch.org/fact-tank/2020/03/06/young-women-often-face-sexual-
harassment-online-including-on-dating-sites-and-apps/> [Accessed 15 March 2020].
2. Dilmaç, B., Aydoğan, D. (2009). Psychological needs as a predictor of cyberbullying:
A preliminary report on college students. Educational Sciences: Theory & Practice,
9, 1035-1038.
3. Duggan, M., (2017). Americans' Online Harassment Experiences. [online] Pew
Research Center: Internet, Science & Tech. Available at:
<https://www.pewresearch.org/internet/2017/07/11/experiencing-online-harassment/>
[Accessed 15 March 2020].
4. Duggan, M., (2017). Online Harassment In Focus: Most Recent Experience. [online]
Pew Research Center: Internet, Science & Tech. Available at:
<https://www.pewresearch.org/internet/2017/07/11/online-harassment-in-focus-most-
recent-experience/> [Accessed 15 March 2020].
5. Duriau, V. J., Reger, R. K. and Pfarrer, M. D. (2007) ‘A Content Analysis of the
Content Analysis Literature in Organization Studies: Research Themes, Data Sources,
and Methodological Refinements’, Organizational Research Methods, 10(1), pp. 5–34.
doi: 10.1177/1094428106289252.
6. Lindsay, M. et al. (2016) ‘Experiences of Online Harassment Among Emerging Adults:
Emotional Reactions and the Mediating Role of Fear’, Journal of Interpersonal Violence,
31(19), pp. 3174–3195. doi:
10.1177/0886260515584344
7. Lindsay, M., Krysik, J. (2012). Online harassment among college students: A
replication incorporating new Internet trends. Information, Communication & Society,
15, 703-719.
8. Schenk, A. M., Fremouw, W. J. (2012). Prevalence, psychological impact, and coping
of cyberbully victims among college students. Journal of School Violence, 11, 21-37.
9. Schenk, A. M., Fremouw, W. J. (2012). Prevalence, psychological impact, and coping
of cyberbully victims among college students. Journal of School Violence, 11, 21-37.
10. Veletsianos, G. et al. (2018) ‘Women scholars’ experiences with online harassment
and abuse: Self-protection, resistance, acceptance, and self-blame’, New Media &
Society, 20(12), pp. 4689–4708. doi: 10.1177/1461444818781324.
0 notes
Text
Post 2 - Discussion of Lecture [Disinformation, Fake News and Surveillance & February 17, 2020] - 800 words
Post-2 (Weeek4): Will personal privacy gradually disappear with the development of the Internet
1.Introduction
Nowadays, we use our mobile phones to browse news videos and write down information we want to know in search engines. We use social networking sites, email, mobile phone location after a call, positioning of mobile applications, etc., and we swipe credit cards Location, the address of online purchases. These seemingly inconspicuous messages are actually our privacy. Imagine that a girl who is pregnant early is afraid that a baby and childcare guide will be sent to her home, and a father who is just out of work will be upset by a job training advertisement that pops up in the browser. Just imagining that strangers get their genetic sequence can be frightening. Released offenders who want to re-employ, may kneel and ask employers not to check their criminal records. The term privacy has been debated by jurists for many years, and it is too complicated to discuss specific projects. There are several levels of protection for specific information. In my opinion, my personal position, whether it is laws or policies, should be to protect the individual's rights and interests. The personal data related rights and interests, if not recognized by the society, or if the platform/enterprise clearly advises and consumers agree, should be given to individuals. There are many non-profit organizations and activities involving environmental and gender issues, but very little privacy or data, especially in China. At the same time, to the extent that individuals can do it, everyone should reflect on and value the security of their privacy.
Personal position, whether it is laws or policies, should focus on protecting individual rights and interests as well as personal data related rights. If it is not a recognized institution or platform in the society or a company clearly informs and consumers agree, rights should be returned to individuals. Nowadays, there are many non-profit organizations and activities related to the environment, gender and other issues, but very few related to privacy or data, especially in China. So, to the extent that individuals can do it, everyone should reflect on and value the security of their privacy.
2. Privacy has been recorded
There are many unique aspects of privacy issues. One is extremely serious information asymmetry. If you are not very familiar with the relevant disciplines, it is difficult for individuals to figure out what information they have collected, who collected it, and what it did. After the search engine searches, it is quite normal for the website to pop up keyword advertisements immediately. Taxi software may record your movements, search engines may record the keywords of diseases you search for, and social media will faithfully record your past laughter and appearance. Employers, private hospitals, and insurance companies you know in the future may be interested in this information. It is also difficult for many individuals to imagine how data is used in enterprises. For example, in 2009, American scholars pointed out that public information can be used to infer the social security number (SSN) (Acquits and Gross, 2009). Another great example in academia is the use of social network content and friend relationships to infer sexual orientation (Jernigan and Mistree, 2009).
The second point about the uniqueness of privacy issues is that you may be unable to recover privacy. As mentioned earlier, it is difficult to imagine what a company does with personal information, including the possibility that the company may sell your information to others. If you search for the keyword "sneakers" in the search engine, this information may be immediately imported into a huge database, together with hundreds of thousands of other people ’s search records, auctioned in real-time, and then formed into advertisements, "just happens" displayed Before you are about to watch a TV series. You are thus passively received the information, but you have nothing to do.
Another aspect of the uniqueness of privacy issues is that new personal images on the Internet social platform you personally create will also be discovered and revealed by others (Trottier, 2012). Make your own privacy decisions every day about what you need to share or how much to expose to whom (SE, 2018). Even if individuals take good care of their social platforms and strive to dress up all their information, social platforms can still infer which people are you, such as your sexual orientation, from the public information of friends and relatives. At the same time, the more people around you use social software or platforms, the greater the personal pressure (Trottier, 2012). At the same time, even if you don't provide information, as long as you provide enough individuals like you, your efforts are futile. Maybe a man working in office A is reluctant to reveal his home address and does not want to let people know his personal tastes and preferences, preventing companies from using his home address or eating taste to cause unnecessary trouble, but As long as his / her co-workers or his / her neighbors display the information, and he and these people are connected through one or more software, his preferences will still be discovered, and she still has no way to Very good escape. Considering many learning characteristics, the more information you expose, the more likely it is that new disclosure will have an impact.
3. Conclusion
The previous statement may give the impression that big data is not good. But in fact, it is not difficult to find that the advancement of data science has brought benefits to society. From various sharing economies to comprehensive social platforms, many redundant resources are used, and any information that was once impossible to communicate is quickly integrated to form new knowledge. New relationships are formed in a vast area. The society enjoys a lot of benefits from it. However, the problems mentioned earlier do exist
The European Union was the earliest, with relatively strict laws in the late 20th century. The United States also strengthened privacy protections in the early 2000s and restricted online data collection. China has just passed the Cybersecurity Law. It can be expected that related non-profit organizations will also rise. The future will only get better.
4. Reference
Acquisti, Alessandro, and Ralph Gross. "Predicting Social Security numbers from public data." Proceedings of the National Academy of Sciences 106.27 (2009): 10975-10980.
Jernigan, Carter, and Behram FT Mistree. "Gaydar: Facebook friendships expose sexual orientation." First Monday 14.10 (2009).
Igo, SE 2018, The Known Citizen : A History of Privacy in Modern America, Harvard University Press, Cambridge. Available from: ProQuest Ebook Central. [17 February 2020].
Trottier, D 2012, Social Media as Surveillance: Rethinking Visibility in a Converging World, Taylor & Francis Group, Abingdon. Available from: ProQuest Ebook Central. [17 February 2020].
VIDEO:https://abcnews.go.com/Technology/facebook-tracking-scrutiny/story?id=14960711#.T0ub1cxvbOX
1 note
·
View note
Text
Post 1 - Discussion of Lecture [Self-presentation and its impact on social media & Monday, February 17, 2020] - 800 words
Post-1 (Weeek3): Self-presentation and its impact on social media
1.Introduction
With the increasing popularity of social media, social media has become a new platform for people to show themselves. Self-presentation in social media is a more specific behavior of social media. This is the main starting point for individuals to use social media, which means that individuals control the presentation of self-related information online and then consciously control others to form A process of self-impression.
In the past, the process of knowing people or things and wanting others to understand themselves was the simplest process, such as postcards, telephones, and newspapers. But after that, the Internet has enabled us to discover what is happening in the world in the shortest time in the fastest and most convenient way and to share important information with friends and family. There are WeChat, Weibo, Facebook and many other social software and platforms in other countries in China. Facebook reached a total of 901 million users (Chen & Marcusb, 2012). 4.75 billion pieces of content are shared every day. Studies show that individuals use social networking services for a variety of activities, including maintaining existing relationships, making new friends, killing time, self-expression, student and political activities, as task management tools, and for learning purposes( (Chen & Marcusb, 2012). A typical college student spends 10 to 60 minutes a day on Facebook (Chen & Marcusb, 2012)and often participates in self-disclosure and presentations to a wide audience on the Internet (Chen & Marcusb, 2012). The speed and number of information interactions are increasing every day.
2. Personal display
Nowadays, social networks have become an important tool and platform for individuals to display themselves. Individuals use social networks to express their ideas and opinions, and they also use social networks to follow other people's information and extend their interpersonal relationships in real life (Tosun, 2012). Individuals present themselves on the Internet, and at the same time browse other people's information on the Internet, it will inevitably lead to social tendencies. The self-displayed on the Internet may be different from the actual self, so why does this phenomenon occur? Whether the differentiation and identification of Internet roles and roles in real life are conducive to the formation of a perfect and clear self-concept of the individual; at the same time, the degree of satisfaction of the individual's basic psychological needs on the Internet, especially the degree of satisfaction of relationship needs in real life. Whether the individual self-knowledge has the function of construction and expansion. The relationship needs are the natural needs of the individuals and can promote the formation of social relationships. Whether this satisfaction of the individual needs is conducive to the formation of a complete and clear self-concept is an issue discussed in this study.
3. Different facets
On the Internet platform, trying to create a character that is completely different or slightly different from reality, may essentially require the existence of a dual personality, or the personal role cannot be satisfied in real life, so I try to use the Internet Build your own role on the platform. You can reshape your character, favorite colors, appreciated works, and hate things (Tosun, 2012). This may be something that you are not allowed to do in peacetime or feel that you are wearing colored glasses and cannot be treated fairly. These are the differences between the self-displayed on the Internet and the real self. In the past, I might think that in real life your preferences should be displayed on the social network platform. They should be the same. But now I don't think there are any unacceptable shortcomings between social platforms and reality.
At the same time, I agree that this differentiation of Internet roles and roles in real life is also considered to be conducive to the formation of a perfect and clear self-concept of the individual because maybe there are many real factors that may restrict us. However, we should not stop learning or progress. We must first make a conceptual framework on the Internet platform, and we can try our best to achieve it when realistic conditions allow. This is very helpful for us to perfect ourselves and achieve the goals that individuals want to achieve. It can be said that it is a virtual power.
4. Conclusion
Besides, social media situations are very different from real situations. Personal disclosures are different online and personally, and culture and personality are important. Specifically, it was found that collectivist individuals who are less extroverted and less interactive in an online environment have disclosed the most dishonest and audience-related information compared to others. (Chen & Marcusb, 2012) The exploratory analysis also shows that students use websites like Facebook primarily to maintain existing relationships, this may include personal relationships, social interaction and the ability to organize groups. It is undeniable that this has had a positive impact on the participants in social networks to some extent.
5. Reference
Chen, B. & Marcusb, J., 2012. Computers in Human Behavior. Students’ self-presentation on Facebook: An examination of personality and self-construal factors, 11, pp. 2091-2099 .
Tosun, L. P., 2012. Computers in Human Behavior. Motives for Facebook use and expressing “true self” on the Internet, 7, pp. 1510-1517.
1 note
·
View note