#retransmission
Text
Error Detection And Correction In CAN: Ensuring Reliability In Automotive Networks

INTRODUCTION
Communication is essential in the ever-changing world of automotive technology. Modern vehicles come with a variety of technological systems that must work in perfect harmony with one another. The Controller Area Network (CAN), a strong and dependable protocol that facilitates data interchange across multiple components, is one of the cornerstones of this communication. However, procedures for Error Detection In CAN and correction are essential for maintaining this reliability. We will delve deeply into the area of Error Detection In CAN and correction in CAN in this 1500-word blog post, learning the significance of these procedures in guaranteeing the safety and dependability of contemporary cars.
The Importance of CAN in Contemporary Automobiles
Let’s first examine the function of CAN in contemporary autos before moving on to error detection in CAN and rectification.
CAN, what is it? Vehicle electronic control units (ECUs) may communicate with one another thanks to the strong serial communication protocol known as the Controller Area Network.
Why Is It Important? By enabling real-time data sharing between ECUs in charge of tasks like engine control, transmission management, and safety systems, CAN has emerged as the foundation of automotive communication.
1. The Vulnerability of CAN

Error Detection And Correction In Can | Dorleco
Even though CAN is very dependable, mistakes can still happen. Several things can cause communication errors, including:
Noise and interference: The electromagnetic interference produced by numerous electrical components in the vehicle environment, which is noisy, can taint CAN messages.
Hardware faults: Defects in transceivers or other hardware parts may result in CAN communication faults.
Electromagnetic Compatibility (EMC): Problems with compatibility between different ECUs and CAN components can also cause communication difficulties.
2. The Basics of Error Detection in CAN
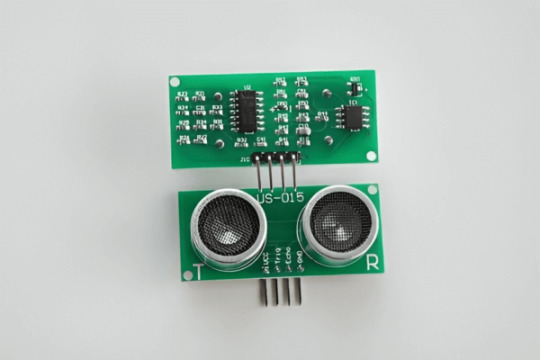
Error Detection And Correction In Can | Dorleco
A variety of Error Detection In CAN mechanisms are used by CAN to preserve dependability.
The Cyclic Redundancy Check (CRC) algorithm creates a checksum depending on the transmitted data. To find errors, the receiving node computes its CRC and compares it to the transmitted CRC.
Similar to CRC, the FCS field in the CAN frame carries checksum information used for error detection.
Bit Stuffing: CAN use bit stuffing to make sure that the sender and receiver are in sync. The bit packing pattern may deviate, which could mean there is a problem.
3. Error Correction In Can
Although Error Detection In CAN is important, there are times when it is insufficient. Error-correcting techniques go one step further:
Retransmission: When an error is found, the sender sends the message again. This guarantees that the message is appropriately delivered to its target.
The CAN protocol has an acknowledgment mechanism that allows the receiver to confirm that a message was successfully received. The sender retransmits if no acknowledgment is received because they presume an error.
4. Error Recovery and Handling
It is essential to comprehend how CAN manages faults and bounces back to ensure system dependability:
Error Flags: CAN employ error flags to indicate various faults. These warning signs aid in identifying and fixing problems.
Error Passive and Error Active States: Depending on the number of mistakes found, CAN nodes can flip between error passive and error active states. This lessens the likelihood that errant nodes may disrupt the network as a whole.
5. Advanced Error Handling Strategies
Advanced error-handling techniques are sometimes used to guarantee ongoing communication:
Fault-Tolerant CAN (FTCAN): FTCAN is a redundancy-based strategy that employs two CAN buses that run concurrently to ensure that communication can continue even if one bus fails.
Flex Ray: Flex Ray is a different communication standard used in automotive networks that offers improved error-handling capabilities but is not a CAN protocol.
6. Security and Error Detection in CAN
Security is a major worry as connected and autonomous vehicles proliferate. It’s critical to comprehend how mistake detection relates to security:
Cyber security: To prevent unauthorized access and manipulation, effective Error Detection In CAN and correction methods are essential. Malicious assaults on CAN networks are a possibility, which underscores the need for these mechanisms.
Intrusion Detection Systems: To recognize and address security threats, cutting-edge intrusion detection systems are being integrated into CAN networks.
7. The Future of Error Detection and Correction in CAN
The future of Error Detection In CAN and correction in CAN holds intriguing advances as vehicles become more complicated and connected:
AI-based algorithms based on machine learning can help identify and repair problems in real-time while responding to changing circumstances and threats.
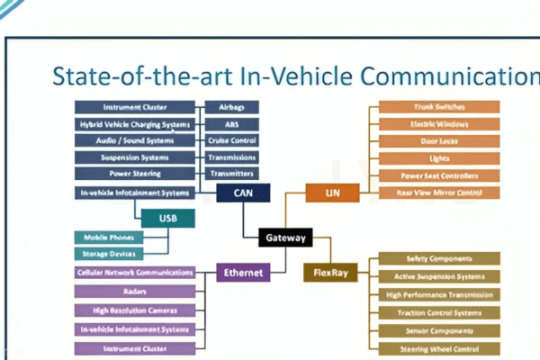
Error Detection And Correction In Can | Dorleco
Blockchain Technology: It is being investigated how to use blockchain for tamper-proof and secure data capture and transfer.
Conclusion
The Heartbeat of Contemporary Vehicles
In conclusion, the Controller Area Network (CAN) is the unsung hero of contemporary automobiles since it makes it possible for crucial electrical component communication. Unsung heroes working behind the scenes to keep this communication dependable, secure, and safe are Error Detection In CAN and correction procedures. The significance of reliable error handling in CAN will only increase as vehicles continue to develop and adopt new technologies. It’s important to get from point A to point B securely, effectively, and with the knowledge that all of your car’s systems are working together as they should. This is made possible by Error Detection In CAN and repair, which will continue to be crucial to the industry’s ongoing evolution.
#Errorcorrection#CAN#Dorleco#errordetection#errorRecovery#Retransmission#automotivenetwork#automobiles
0 notes
Text
novinha dando conta de uma suruba tres machos
Mexican couple having hard sex
Indian bathroom selfie
Blonde girl orgasm with dildo creamy pussy masturbate
MILF STORIES #1 Lusty STEP MOM fuck with step son while dad working
Cogiendo a la gordibuena de mi vecina en tanga la perra
Horny babes licking and fucking toys in outdoor lesbian orgy
Cute indian gay showing his big dick and masturbating
Young slut Milla Mason walks in on older stud having a shower and they fuck on the bathroom floor
Hawt chick gets licked at gloryhole and slimed by fake dick
#shapometer#hashing#scentwood#plicatile#Mans#solidifier#retransmission#Vada#corrive#excruciatingly#gonimoblast#noneastern#lavs#alkitran#unacquit#infinito-absolute#heeders#quasi-foolish#baleare#sycophantically
0 notes
Text

La tournure anglicisée :
en replay
souvent utilisée dans le langage télévisuel, peut être évitée et remplacée par les termes suivants :
en rediffusion à la demande
en rattrapage [Québec]
Quant au substantif :
le replay
il peut être rendu en français par les termes suivants :
la rediffusion à la demande
l'émission de rattrapage
On rencontre également :
la retransmission à la demande.
Évitons l'utilisation abusive de mots d'origine anglaise, qui la plupart du temps ont leurs pendants français, plus facilement compréhensibles !
👉 Pinterest : en rediffusion à la demande / en replay
11-08-2022
#replay#rediffusion#demande#rattrapage#émission#retransmission#anglicismes#franglais#globish#néologismes#neologisms#français#french#langue française#french language#mots français#french words#termes français#vocabulaire français#french vocabulary#anglais#english#frenchblr#french langblr#french studyblr#french stuff#french vocab#french learning#learn french#language learning
0 notes
Text
The Concept of Edge Computing - By Azgari Lipshy
To reduce the amount of data transmission and storage required, many organizations are turning to a technique called "edge computing," in which computations are performed at or near the point where data is being generated.
“The time when people owned computers is long gone. Power and connectivity are the most important things in computing right now.”
Edge computing is a shared information technology architecture that brings data storage and computation closer to data sources like local edge servers and IoT devices. But that isn’t all there is to know about edge computing. In this article, I’ll comprehensively explain the meaning of edge computing, how it works, its importance, and its uses!

Meaning of Edge Computing
Edge computing is capturing, keeping, processing, and examining data close to the client, where the data originated from. It transmits some parts of data and storage resources in the central data center closer to the data source. Instead of transmitting raw data to the primary data center for analysis and processing, that work is done at the origin of the data, whether it's a factory store, retail store, or across cities.
The result of the computing work at the edge, like maintenance predictions, or real-time business insights, is sent back to the central data center for analysis and other human interactions. It is safe to say edge computing is modifying business and IT computing.
How Edge Computing Works
Edge computing has to do with location. In existing enterprise computing, data is generated at a client's endpoint, like a user's computer. The generated data is then moved across a Wide area network (WAN), like the internet, through the corporate Local area network(LAN). The data is kept and worked on by an enterprise application. The work results are then transferred back to the client's endpoint. This is a proven approach to client-server computing for many standard business applications.
But the amount of internet-connected devices, and the size of data generated by those devices and utilized by businesses, is growing too rapidly for existing data center infrastructures to take in. The idea of edge computing isn't new. It is deeply rooted in years-old ideas of remote computing, like branch offices and remote offices. It was more efficient to put computing resources at the location of choice instead of relying on one central location.
Edge computing places servers and storage where the data is, often needing more than an incomplete gear rack to work on the remote Local area network to gather and locally process the data. In most cases, the computing gear is used in hardened or shielded enclosures to safeguard the gear from moisture extremes and every other environmental condition. Processing involves analyzing and normalizing the data stream to search for business intelligence, and only the analysis results are sent back to the central data center.
Why is Edge Computing Important?
Computing tasks need compatible architectures, and the architecture compatible with one type of computing task might not fit every computing task. Edge computing has become a vital and viable architecture that supports shared computing to use storage and compute resources closer to the exact physical location of the data source. Generally, shared computing models are barely new, and the concept of data center colocation, cloud computing, remote offices, and branch offices have a trusted and proven record.
Edge computing has significantly grown because it provides solutions to new network problems related to moving large volumes of data that present-day organizations develop and consume. It's not only a matter of amount but also time. Applications rely on time-sensitive responses and processing.

Principle Network Limitations Addressed by Edge Computing
Consider the call to fame of self-driving cars. They rely on intelligent traffic control signals. Traffic and Car controls are required to produce, examine and swap data in real-time. Multiply the large numbers of autonomous vehicles by the requirement, and the scope of the possible problems becomes clearer. To solve the problem, a responsive and fast network is needed. An effective edge computing model should be able to address three significant network limitations: Latency, bandwidth, and reliability or congestion.
1. Bandwidth: Bandwidth is the data size a network can carry over some time, in bits per second. Every network has finite bandwidth, and the restraints are more severe for wireless communication. There is a limit to the amount of data or devices that can convey data across the network. While it is possible to boost network bandwidth to allow more data and devices, it can come at a high cost, there are higher limits, and it doesn't resolve other problems.
2. Latency: Latency is the time required to transmit data from one point to another on a network. While communication occurs at the speed of light, long physical distances, together with network outages or congestion, can delay the movement of data over the web. This can delay the decision-making and analytics processes and, at the same time, reduce system responses in real time.
3. Congestion: The internet is a universal "network of networks." Although it has developed to provide excellent general-purpose data swaps for major everyday computing tasks like basic streaming or file exchanges. The size of data associated with billions of devices can overwhelm the internet, which causes congestion and forces time-consuming data retransmissions. In other cases, network congestion or outages can worsen congestion and even cut off some users' communication entirely, rendering the IoT useless during outages.
By utilizing servers and data storage sources, edge computing can work on many devices over a more efficient and smaller local area network where sufficient bandwidth is exclusively used by local data-generating devices, thereby addressing the issue of congestion and latency.
Local storage gathers and secures the raw data. In contrast, local servers can execute crucial edge analytics or reduce the data to make real-time decisions before transmitting results to the central data center or the cloud.
Conclusion
Edge computing assists in unlocking the potential of the numerous untapped data generated by connected devices. By employing edge computing models, you can increase operational efficiency, discover new business opportunities, and provide more reliable and faster experiences for your customers.
About Author
Azgari Lipshy is passionate and writes about technology, yoga, and her solo travels worldwide.
0 notes
Text
youtube
Full recording of the retransmission of Lovejoy's gig at Open'er Festival!
#lovejoy#wilbur soot#ash kabosu#mark boardman#joe goldsmith#open'er festival#festival summer 23#Youtube
132 notes
·
View notes
Text

U.S. Navy declares IOC for its new UAS reconnaissance MQ-4C Triton
Fernando Valduga By Fernando Valduga 09/15/2023 - 14:00 in Military, UAV - UAV
The U.S. Navy officially declared the initial operational capability (IOC) of Northrop Grumman Corporation's MQ-4C Triton multi-manned unmanned aircraft on September 14.
Since its Early Operational Capability (EOC) milestone in May 2020, the MQ-4C Triton has operated within the U.S. Navy Pacific Fleet, conducting maritime intelligence, surveillance and reconnaissance (ISR) missions in the area of responsibility of the U.S. Indo-Pacific Command as the Navy's only unmanned, high-altitude, long-lived aircraft.
The MQ-4C Triton, manufactured for use by the U.S. Navy and the Royal Australian Air Force (RAAF), supports a wide range of missions. These include maritime patrol, signal intelligence, search and rescue operations, as well as communications relay tasks.
According to the producer, these aircraft offer persistent surveillance capabilities, assisting in predicting opposing actions and facilitating more effective joint military efforts and enterprises.

Operating at altitudes above 50,000 feet and boasting a 24-hour resistance, the Triton serves as a continuous communications retransmission center, ensuring connectivity between dispersed Navy units, while allowing commanders to operate with a shared operational overview.
“The Triton proved to be invaluable for the maritime patrol and reconnaissance mission in the Indo-Pacific. Now that the system has reached its initial operational capacity, commanders will be able to take full advantage of Triton's powerful set of sensors to detect and stop potential opponents around the world," said Rho Cauley Bruner, director of the Triton program at Northrop Grumman.
"The persistent global maritime awareness is fundamental to deter, or compete and win, our opponents. Triton ensures that we are making informed decisions and operating effectively anywhere in the world," added Captain Josh Guerre, manager of the U.S. Navy's persistent unmanned aircraft systems program.
Northrop Grumman provided the U.S. Navy with a total of five Triton aircraft equipped with multiple intelligence capabilities, with the most recent delivery occurring in June 2023.
Tags: Military AviationNorthrop Grumman MQ-4C TritonUASUSN - United States Navy/U.S. Navy
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
MILITARY
Lockheed Martin receives US$ 151.4 million to manufacture F-16 Block 70 fighters for Bulgaria
15/09/2023 - 13:00
MILITARY
Bell and USAF will test high-speed vertical takeoff and landing module
15/09/2023 - 11:00
MILITARY
Denmark welcomes the first four F-35 fighters that land on Danish territory
09/15/2023 - 08:29
BRAZILIAN AIR FORCE
FAB C-130 Hercules aircraft uses Datalink Engine Tactical System in SAR training
09/14/2023 - 20:00
MILITARY
Aeralis presents improvements in the concept of Airflex modular combat coach
09/14/2023 - 16:00
MILITARY
The second KC-130J destined for Germany flies
14/09/2023 - 15:00
30 notes
·
View notes
Text
@canonkalluzeb It's an attempt in mirroring terminology of IRC, which does not necessarily makes sense in context of Discord, and Discord knows this perfectly well because they're both internally, and also among programmers who make Discord bots, called "guilds", not "servers".
Some background: when two computer applications on two separate computers have to communicate, one of them has to first set up the connection, and so the program which listens to connections is often called "server", and the program which attempts to connect is called "client", which is an analogy of how restaurants work.
And of course it's not like two arbitrary programs can understand each other, so when one needs to make two programs communicate with each other, one designs a "protocol", which is a description of the exact rules these two programs are supposed to interact on.
Back in The Old Days (90s to early 00s) the most common protocol for chat-like applications was called IRC (Internet Relay Chat), which does follow the "client-server architecture", where someone (could be anyone, but usually it was universities or ISPs) runs the IRC server application on their computers, and people who want to chat, run IRC client applications which connect to these servers.
(it is still possible to use IRC today, but a lot of people don't because the newer alternatives provide features which people are used to, like... file upload/storage, persistent chat history, or transport encryption)
On the most basic level, a person that uses an IRC client first makes it connect to an IRC server by typing an address to connect to, and then picks the channels to join there, of which each functions as an independent conversation, in that
your IRC client usually displays the chat messages grouped together by the channel
the clients which joined a channel can send a message to this channel, which server receives...
...and then sends it to every other client which joined such channel
the clients which did not join a channel do not receive messages that are sent to the channel
if your client did not receive a message (due to lost connection, or maybe you were not in the channel in the first place), you will not see this message ever again, as IRC has no mechanisms of providing you a message history, nor retransmission of earlier messages
it may be possible for a regular user to create a channel, depending on how the IRC server is configured
Now here's how Discord works:
you are not supposed to run a Discord server application. Discord (the company) made one, and it is running on their computers (the ones they manage at least), but you can't run it on your computer (for whatever reason you wanted to do so), because they won't give it to you in the first place
the only thing you are supposed to run, is the Discord client application, which they offer to you for free
since no one outside of Discord (the company) is supposed to run Discord servers, the fact you're connecting to them specifically is not supposed to be relevant to the end user
your Discord client maintains a connection to a Discord server, which sends real-time information on stuff like "there is an unread message on guild number 253958353" or "you got pinged in a direct message by user with number 34235936984" to the client
any user can create a "guild", of which the person who created it is marked as a "guild owner", which is highest possible rank and everyone else on the server can only be a granted permission to do a subset of actions a server owner can do.
a guild has a list of channels, a list of users joined it, and a list of roles
roles can be assigned to the user, and apply within a guild only
a role controls the list of possible actions a user can do in the context of the server
a channel functions as a chronologically-sorted list of messages, of which you can retrieve a part of it by clicking on it, and other parts - by scrolling
Now take this into account that what I've just called "Discord server" is usually not something the end user needs to worry about, so it's typically not mentioned at all, and "guild" is called "server" literally everywhere else outside of developer documentation, and you can see why this feels a bit confusing.
#mlem's computing stuff#my apologies to the person I pinged because I think I stopped making this post an explanation towards them in around the middle of it#and made it into a discord terminology rant instead#discord
13 notes
·
View notes
Text
The man, the myth, the legend, who inspired some of my takes for Tobias' rapid rise to opulence:
"During the early stages of World War II, Pujol decided that he must make a contribution "for the good of humanity" by helping Britain, which was at the time Germany's only adversary. He approached the British Embassy in Madrid three different times, but they showed no interest in employing him as a spy. Therefore, he resolved to establish himself as a German agent before approaching the British again to offer his services as a double-agent.
Pujol created an identity as a fanatically pro-Nazi Spanish government official who could travel to London on official business; he also obtained a fake Spanish diplomatic passport by fooling a printer into thinking Pujol worked for the Spanish embassy in Lisbon. His instructions were to move to Britain and recruit a network of British agents. He moved instead to Lisbon; – using a tourist's guide to Britain, reference books and magazines from the Lisbon Public Library, and newsreel reports he saw in cinemas – created seemingly credible reports that appeared to come from London. He claimed to be travelling around Britain and submitted his travel expenses based on fares listed in a British railway guide.
During this time he created an extensive network of fictitious sub-agents living in different parts of Britain. His reports were intercepted by the British Ultra communications interceptions programme, and seemed so credible that the British counter-intelligence service MI5 launched a full-scale spy hunt. The British had become aware that someone had been misinforming the Germans, and realised the value of this after the Kriegsmarine wasted resources attempting to hunt down a non-existent convoy reported to them by Pujol.
Pujol wrote 315 letters, averaging 2,000 words, addressed to a post-office box in Lisbon supplied by the Germans. His fictitious spy network was so efficient and verbose that his German handlers were overwhelmed and made no further attempts to recruit any additional spies in the UK. The information supplied to German intelligence was a mixture of complete fiction, genuine information of little military value, and valuable military intelligence artificially delayed.
For radio communication, he needed the strongest hand encryption the Germans had. The Germans provided him with this system, which was in turn supplied to the codebreakers at Bletchley Park. His encrypted messages were to be received in Madrid, manually decrypted, and re-encrypted with an Enigma machine for retransmission to Berlin. Having both the original text and the Enigma-encoded intercept of it, the codebreakers had the best possible source material.
On occasion, he had to invent reasons why his agents had failed to report easily available information that the Germans would eventually know about. For example, he reported that his (fabricated) Liverpool agent had fallen ill just before a major fleet movement from that port, and so was unable to report the event. To support this story, the agent eventually "died" and an obituary was placed in the local newspaper as further evidence to convince the Germans. The Germans were also persuaded to pay a pension to the agent's (also fabricated) widow. The Germans paid Pujol US$340,000 over the course of the war to support his network of agents, which at one point totaled 27 fabricated characters."
#muse: tobias.#* tobias. / development.#ask to tag#This man was such an icon I can't even UADUISADHSAD8AIDU#Tobias 1000% did something similar except on a much larger scale (not just 2 countries; and not only in the military dept)#The sheer amount of aliases Tobias has by the time he turns 21 almost rivals L's own 😭😭😭#If one day Wammy's decides to hunt him down it'd be such a hilarious experience bc they'd realize he's intrinsically tied to EVERY#field you can possibly think of; and has allies that'd stop any investigation on his behalf thru any means necessary w/o him asking them to#Some of these connections are genuine; some are completely fabricated like above ^; some are thru blackmail; some are thru other allies etc#'Which country is he loyal to?' None; next question! ADHSAUIDSJASDK in theory it should be the UK bc of his upbringing but#precisely BECAUSE of his upbringing it isn't the UK. His only allegiance is to Wammy's House and even that is... dependent on the context#I mean he accomplishes his role as a 'safeguard of peace' as per Wammy's wishes/goals; but he has Such a chaotic way of doing so...#He considered the US for a bit too but the vice president cheering on Kira irritated him enough that he dismissed that idea
2 notes
·
View notes
Text
youtube
JEUDI 28 MARS 2024 (Billet 3/3)
« MONDIAUX DE PATINAGE ARTISTIQUE (Canada – Montréal) »
Le Français Adam Siao Him Fa a remporté la Médaille de Bronze samedi aux Mondiaux de patinage à Montréal, à la faveur d'une incroyable remontée dans une compétition gagnée par l'Américain Ilia Malinin.
19e après le programme court mercredi, Adam Siao Him Fa a merveilleusement réagi sur le programme libre pour s'offrir, après une longue attente, la médaille de bronze dimanche aux Mondiaux de Montréal (Canada).
Le Français de 23 ans a maîtrisé tous ses envols, notamment ses quatre quadruples (lutz, salchow et deux boucles piqués, dont un en combinaison avec un triple) et même abandonné sciemment deux points en s'autorisant un backflip (salto arrière), figure interdite qui le caractérise et qui a provoqué l'ovation du public du Centre Bell.
C'est la première médaille française chez les hommes depuis 14 ans (depuis celle de Brian Joubert en 2010) !
« Ce Championnat a été synonyme de hauts et de bas pour moi. Cela a été beaucoup d'émotions, a réagi Adam Siao Him Fa. Je suis content d'avoir pris ma revanche par rapport au programme court, c'est vraiment ce que je voulais », a-t-il ajouté, évoquant « la meilleure performance » de sa vie. Le Français avait remporté en janvier dernier un deuxième titre de Champion d'Europe.
(Source : « lequipe.fr »)
___________________________
Il fut un temps où les Championnats de Patinage Artistique étaient diffusés à la télévision sur une grande chaîne nationale. Malheureusement cette époque est révolue, il faut aujourd’hui être abonné (en payant) à la chaîne « L’Equipe ». En revanche, le téléspectateur peut n’échapper à aucun match de football ou de rugby. Parfois même, un programme initial est remplacé au dernier moment par la retransmission d’un de ces matchs !
Et c’est bien dommage, surtout pour ceux, comme nous, qui n’en regardons jamais ! Si c’est un problème d’audience, pourquoi le patinage (dont peut-être l’horrible défaut est d’être qualifié « d’artistique ») n’est pas rediffusé par exemple en seconde partie de soirée sur une chaîne faisant partie de la TNT ?
Nous dédions ce Billet à tous nos lecteurs/abonnés qui se sentent frustrés de cette grave lacune de notre Service Public, dont sûrement notre cousine Catherine (W.B.).
PS Nous avons fait des recherches sur la musique, très particulière, choisie par le jeune patineur français et grâce à Shazam nous avons appris qu’elle était de l’excellent compositeur contemporain, Max Richter et que le morceau s’appelle « Departure », déjà tout un programme.
2 notes
·
View notes
Text
J13 ~ À l'assaut des sommets
León~Ponferrada 105km

Arrivé au bout du plateau, je retrouve la montagne. Aujourd'hui m'attend le plus haut col de mon voyage (enfin je crois ou plutôt j'espère !). Je croise toujours la même route la N120 qui, comme moi, traverse le Nord de l'Espagne d'Est en Ouest. Aussi loin que je m'en souvienne, j'ai commencé à la suivre un peu avant le km 60 !

J'arrive rapidement à Astorga, au pied de la montagne. A côté de la cathédrale, le palais épiscopal est un grand bâtiment aux allures médiévales réalisé par Gaudí. J'en ai vu un à León également (la Casa Botines) mais j'ai eu du mal à le croire tellement le style me semble éloigné du Gaudí que je connais.

Je quitte Astorga. La route monte vraiment doucement. J'attends pendant un moment les choses sérieuses. Quand arrive enfin les plus fortes côtes il ne reste plus qu'une dizaine de kilomètres avant le col.

Si la montée prends du temps, la descente elle est très rapide. Sur un tronçon raide, bien large et dégagé, je bats un record de vitesse sur ma bicyclette : 63,4km/h au compteur !

Fin de journée à Ponferrada et son château planté au milieu de la ville qui semble sortir tout droit d'un conte de fées.

L'auberge est top ! Une dizaine de petits dortoirs répartis sur 3 niveaux, une grande salle à manger, une salle de jeux avec babyfoot, billard, flechettes et retransmission des matchs de la Liga sur vidéo projecteur. L'ascenseur est assez grand pour descendre le vélo au sous-sol où m'attend un grand atelier de réparation de vélo avec tout le nécessaire pour entretenir sa fidèle monture. J'en profite pour faire quelques réglages en prévision de la journée de demain.

🎶
2 notes
·
View notes
Text
Ultimate Alien should have ended with a 20-minutes episode Ben Vs Vilgax-Dagon, with Ben using his ultimatrix to change of appearance during their fight.
With a universal wide retransmission, everyone encountered by the gang during the whole show would be on the edge of their seat, while the two fighters would destroyed Mt Rushmore with fire and energy blasts.
And in the end, it would be Vilgax-Dagon against Diamondhead, George's sword in one hand, a taedenite spear in the other. A long clash until Ben/Diamondhead plunges George's sword in Vilgax, sucking away Dagon (just like in the original show).
That would have been a much more satisfying ending for me
13 notes
·
View notes
Text

the record he's holding is DICE by FLOW, the titular song being the new OP FLOW wrote for the 15th anniversary retransmission of the series.

7 notes
·
View notes
Text
Wait until--probably like, five years from now because my haters are slow as hell--the dots connect on what's going on at the syndication level.
Specifically being, the increased abandonment of TV and transition towards digital, with all these actual stations people invested lots of money in threatening to go obsolete, basically, and send cable in a chaos spiral with it with the way retransmission currently works.
Anti trust laws are good, but have caused a traffic jam, where syndicates can only own so much so close and so on. And same on the other end. We're approaching a day where everything is digital somehow and bypassing classic TV, but that risks putting everything in the megacorp studio hands. So, smart syndicates, like Gray, have invested to become their landlords, by making Studio City. Nexstar is taking other avenues like buying networks.
But most of all, while Nexstar sidesteps that way, Gray knows how to use metro stations very well. But CW metro stations aren't worth the value even Nexstar wants for it for retransmission, which is why we lost 2 of the top 5 metro areas for some weeks while they fought about it.
For socioeconomical and historical reasons I'm not going to unpack in this post (as much as ask others to review my Team Peachtree hashtag), Gray is very happy to take stations when and where they can right now.
Nexstar is essentially in a handshake with Gray right now so dense their presidents are liking each others LinkedIn posts on everything from business, vacation, or discussions of the class gap. Because Nexstar is essentially trying to make stations sustainable enough to be attractive to buy especially for Gray with eyes on spots like DC, because we literally kicked CW in the nuts that hard that everybody ELSE started losing billions.
The dogwhistler's dream squealing from 2po about "conservative owners" is hysterical. No, see, they're the owners of the most CW stations, period. Their goal is money first. And they own the major liberal areas we lost for a bit. Gray owns the rest. Thinking they're gonna sink their value in DC for some backwater station in idaho with 10 viewers is fucking maximum delusional grudgewank as the only real source. That's not how syndicates or TV works. At best, politics influence their daytime local news. Not their primetime national shit. Fuckin hell.
This is so far beyond the scale of the pitiful squealing 2po is doing about a ship he doesn't like. This is about media motions that influence not just CW, but WB proper, NBC, Netflix, CBS and others in huge ways they haven't even tried to conceive wrapping their heads around. It's about black entertainers taking back what's theirs and becoming the leading film mecca that was taken from it years ago. It's becoming old TBS a new way, making sure their content contracts keep their city in every network and every streamer's work into the digital age while running the last waves of TV before resuming high power radio eventually when the digital shift happens. That's it. That's all it is.
5 notes
·
View notes
Text
Blackpink Makes History As First Female Group To Earn Over $3M In A Single Arena Concert
Blackpink Makes History As First Female Group To Earn Over $3M In A Single Arena Concert
INDIO, CA – APRIL 12: (EDITORS NOTE: Retransmission with alternate crop.) (L-R) Jennie Kim, Rosé, Lisa and Jisoo of ‘BLACKPINK’ are seen at the YouTube Music Artist Lounge at Coachella 2019 on April 12, 2019 in Indio, California.
Roger Kisby/Getty Images for YouTube
KEY POINTS
Blackpink’s Newark concerts each grossed $3.298 million
The quartet kicked off their “Born Pink” world tour in South…

View On WordPress
2 notes
·
View notes
Text
Plusieurs millions de personnes sourdes exclues du débat politique
La France compte quatre à six millions de personnes sourdes et malentendantes. Le manque d’accessibilité des débats politiques (interprètes LSF, sous-titrages de qualité) prive ces personnes de leur citoyenneté.
Jeudi 24 mars 2022, plusieurs candidats à la présidentielle étaient invités sur le plateau de France 2 pour débattre sur leurs programmes. Aucune interprétation en langue des signes n’était assurée, le sous-titrage de leurs propos était incomplet et en décalage. À la télévision, les sous-titres étaient illisibles car ils n’avaient pas de fond opaque, au contraire de ceux figurant dans le replay.

Une personne sourde peut-elle saisir les propos de Valérie Pécresse ? Extrait vidéo du replay de l’émission « Élysée 2022 » du jeudi 24 mars 2022, France Télévisions
Comment les personnes sourdes et malentendantes peuvent-elles suivre la campagne électorale et faire leur choix si elles ne bénéficient pas d’une accessibilité totale à l’information ?
Des efforts marginaux
La campagne électorale débute officiellement le 28 mars 2022 mais les douze candidat.e.s à la présidentielle ont déjà entamé leur prospection depuis plusieurs mois. Le CNCPH (Comité national consultatif des personnes handicapées) a lancé le 27 janvier 2022, l’Observatoire de l’accessibilité des campagnes électorales et des scrutins de 2022. Ce dernier publie chaque semaine un état des lieux de la mise en œuvre des dispositions d’accessibilité par les candidates et les candidats à l’élection présidentielle.
Globalement, les efforts sont marginaux : seuls deux candidat.es rendent en partie accessible leur campagne électorale, Anne Hidalgo et Jean-Luc Mélenchon. Le leader de la France insoumise rend accessible les retransmissions simultanées de ses meetings et a diffusé sa profession de foi, ainsi que son programme en langue des signes française. La candidate socialiste signale les informations relatives à l’accessibilité de sa campagne sur son site internet et a également signé le manifeste de la Fédération nationale des Sourds de France.
Non-respect de la législation
La loi du 11 février 2005 pour l’égalité des droits et des chances, la participation et la citoyenneté des personnes handicapées, retient l’interprétation en langue des signes française comme mode d’accessibilité.
Cette loi fait également obligation aux chaînes de télévision publiques et aux chaînes privées dont l'audience nationale dépasse 2,5 % de l'audience totale des services de télévision de rendre accessible aux personnes sourdes ou malentendantes la totalité de leurs émissions, en dehors des messages publicitaires et de quelques programmes dérogatoires.
En ce sens, l’Arcom a émis des recommandations pour l’accessibilité des chaînes télévisées et des clips de campagne. Encore faudrait-il qu’elles soient suivies par les candidats…
2 notes
·
View notes
Text

DARPA wants to prepare laser-equipped tankers to recharge drones
Fernando Valduga By Fernando Valduga 06/15/2022 - 08:08 AM in Military, Technology
The Defense Advanced Research Projects Agency is seeking to explore the potential of transforming existing tankers into so-called "power wells in the air" that can use laser beams to send wireless energy to drones.
Agency employees want industry feedback on the possibility of adapting air refueling aircraft such as the KC-46 and the ?? Air Force KC-135 with "a power transmission pod under the wings" to wirelessly recharge a fleet of unmanned aerial systems, according to a request for information (RfI) published on Tuesday (06/14).
The request, which sets a deadline for shipping July 11, notes that this solution “must have enough power for a continuous wave laser of 100 [kilowatts] or more, as well as thermal control to integrate the laser” into tankers.
The warning aims to evaluate the broader feedback of respondents about the industry's confidence in the creation and testing of these components and subsystems, as well as the associated challenges of adapting equipment and missions to this new feature.
As for the drones themselves, the benefits of designing UAS to receive targeted energy, says RfI, are extended range and operation, in addition to reducing the weight of the organic energy storage of vehicles.
An in-air energy well, says the RfI, can become part of "a more expansive power generation power grid, transfer retransmissions and receiving solutions, allowing the Department of Defense to dynamically allocate energy resources to provide military effects with more flexibility".
Authorities are looking to use the RfI as a starting point, as they evaluate and develop the ability of aircraft to “dynamically transfer energy over a network” of platforms with the capabilities to transmit energy and receive it, according to the warning.
Source: Inside Defense
Tags: Military AviationDARPAKC-46A PegasusTechnologyUSAF - United States Air Force / U.S. Air Force
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in a specialized aviation magazine in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation
HOME Main Page Editorials Information Events Collaborate SPECIALS Advertise About
Cavok Brasil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
History
Military
Brazilian Air Force
Space
SPECIALS
Cavok Brasil - Digital Tchê Web Creation
10 notes
·
View notes