#information security
Text
psst, let me tell you a secret
are you listening?
ready?
Tumblr Blaze is the biggest fuck-you to Facebook, Twitter, Google, Amazon, and other advertising companies in basically ever
wanna know why?
On Facebook, I could show this post only to white, politically undecided, lesbian college students aged 18-21 who live in zip codes 75023, 75024, and 75025 (yes, even after the changes Facebook recently announced). Anyone who interacts with the post, therefore, is extremely likely to be a white, politically undecided, lesbian college student aged 18-21 who lives in Plano, Texas. If this post was an ad, and you clicked the ad and bought the thing it was advertising, then I’d also know your name, physical address, telephone number, email address, and approximate financial status.
You probably don’t want me to know all that about you, right?
Do you want your health insurer to know? What about your employer? If you’re queer and not out to your family and friends, would you want them to know? What if you’re a domestic violence survivor, hiding from your ex-spouse?
All they need to do to get all that information is buy a Facebook ad for under $5.
And before you say that you don’t share all that on Facebook: too bad! Even if you don’t, Facebook (along with pretty much every ad company out there) buys, sells, and/or trades the data it collects about you with other companies. Facebook collects data about you even if you don’t have a Facebook account.
Wanna know what’s scarier?
Bad guys can also buy targeted ads, and use them to convince you to do things like vote for a particular presidential candidate, or vote against unionizing Amazon workers. This is a very common tactic used by hostile foreign governments to foster extremism and isolate vulnerable minorities, and influence elections and other political and social events. Even the tech companies themselves can and do use this data to manipulate your emotions, making you happier or sadder according to their own whims.
(why do you know all this, Sanity? because I’ve worked in information security, fighting for data privacy and security, for over a decade)
Facebook, Google, Twitter, Amazon, and other advertisers claim that collecting all that data about you, and letting anyone target you with it, is absolutely, 100% necessary for the existence of the entire ad-funded Internet. They want you to believe that nothing bad could possibly come of it, despite proof to the contrary being in the news every other month. They want you to blindly continue letting them collect and use YOUR data to influence you to think, feel, and do what THEY want.
But.
BUT!!!
Enter Tumblr Blaze.
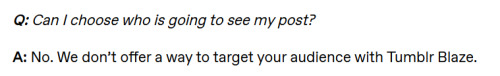
(from the Blaze FAQ)
Tumblr looked at advertising and said, you know what? we don’t need to target anyone. Targeted ads don’t actually work anyway. All that hyper-specific targeting is just an excuse for ad companies to raise prices and collect more data to use for their own purposes.
Tumblr said, we bet people will pay real-life dollars to share their posts with up to 50,000 people, whether or not those people will care.
Tumblr said, we’re going to blow up the entire online advertising industry.
That is fucking amazing, y'all.
#information technology#information security#data privacy#data protection#tumblr blaze#sanity talks a lot
15K notes
·
View notes
Text
He's making a database. He's sorting it twice. SELECT * from contacts WHERE behavior = 'nice' SQL Clause is coming to town. 🎄🎅

569 notes
·
View notes
Text
idk when they did it, but I logged on to my youtube account today to see that Google had CHANGED MY FLIPPING ACCOUNT NAME from the one I CHOSE for it to some unholy amalgamation of numbers and the fakename I used to make that account and I am Annoyed >:( >:( >:(
anyway I spent the morning fiddling with personal info to try and get it to display the account name instead but idk -_- -__- Obvsl there's SOME way to get it back cuz other ppl have old-style pseuds but either it's through some other method or it takes awhile for google to update their unholy spyware cuz my comments are still displaying under that stupid appellation. Gods, I cant imagine how frustrating that must be to ppl who used their actual assigned names when making gmail accounts 15 fucking years ago; the info I put there isn't even 'real' and it STILL feels like a violation X| WHO THE FUCK IS GOOGLE TO DECIDE HOW I SHOULD BE SEEN BY OTHERS?!?!?!
#Google#The Corporate Internet#Pseudonymity#Information Security#Privacy#Outing#Agency#cantankerous posts
38 notes
·
View notes
Text
The most undervalued, misunderstood job in software is security. If the security team is doing their job right, then the only visible effect is that they'll make features slower to develop, slower to run, more expensive, and sometimes so prohibitively difficult that you have to scrap parts of the feature. If that's the case, then your security team deserves a raise for how much hard work they're doing. When it comes to security, anything noticeable happening is VERY BAD.
#codeblr#progblr#information security#the second most undervalued job is ux#but at least its relatively easier to understand their contributions#except for a11y work#when you make an app usable for blind people or people with mobility issues#the only people who notice the improvement are blind people and people with mobility issues#product owners are not checking how things sound on a screen reader or testing if it works without a mouse
13 notes
·
View notes
Text
reminder that if, like me, you used to use LastPass and moved to a new password manager, go delete your LastPass account.
33 notes
·
View notes
Link
Ring, Amazon’s perennially controversial and police-friendly surveillance subsidiary, has long defended its cozy relationship with law enforcement by pointing out that cops can only get access to a camera owner’s recordings with [the owner’s] express permission or a court order. But in response to recent questions from Sen. Ed Markey, D-Mass., the company stated that it has provided police with user footage 11 times this year alone without either.
Last month, Markey wrote to Amazon asking it to both clarify Ring’s ever-expanding relationship with American police, who’ve increasingly come to rely on the company’s growing residential surveillance dragnet, and to commit to a raft of policy reforms. In a July 1 response from Brian Huseman, Amazon vice president of public policy, the company declined to permanently agree to any of them, including “Never accept financial contributions from policing agencies,” “Never allow immigration enforcement agencies to request Ring recordings,” and “Never participate in police sting operations.”
Although Ring publicizes its policy of handing over camera footage only if the owner agrees — or if judge signs a search warrant — the company says it also reserves the right to supply police with footage in “emergencies,” defined broadly as “cases involving imminent danger of death or serious physical injury to any person.” Markey had also asked Amazon to clarify what exactly constitutes such an “emergency situation,” and how many times audiovisual surveillance data has been provided under such circumstances. Amazon declined to elaborate on how it defines these emergencies beyond “imminent danger of death or serious physical injury,” stating only that “Ring makes a good-faith determination whether the request meets the well-known standard.” Huseman noted that it has complied with 11 emergency requests this year alone but did not provide details as to what the cases or Ring’s “good-faith determination” entailed.
Matthew Guariglia, a policy analyst with the Electronic Frontier Foundation, told The Intercept he encourages any Ring owners concerned about warrantless access of their cameras to enable end-to-end encryption — an option the company declined to make the default setting after being urged to do so by Markey. “I am disturbed that Ring continues to offer, in any situation, warrantless footage from user’s devices despite the fact that once again, police are not the customers for Ring; the people who buy the devices are the customers,” said Guariglia.
Guariglia added that even though the “emergency” exception hypothetically might be warranted in the most dire circumstances, there will always be the risks of “mission creep” and police abuse without any meaningful oversight. “If there is the infrastructure, if there is the channel by which police can request footage without a warrant or consent of the user, under what circumstances they get it is out of our control. I worry that because it’s decided by the police and by somebody at Ring, there will be temptation to use that for increasingly less urgent situations.”
In a statement to The Intercept, Markey said that he believed Amazon and Ring have both lost the benefit of the doubt, despite their purported good-faith efforts. “I’m deeply concerned to learn that the company has repeatedly disclosed users’ recordings to law enforcement without requiring the users’ permission,” the senator added. “This revelation is particularly troubling given that the company has previously admitted to having no policies that restrict how law enforcement can use Ring users’ footage, no data security requirements for law enforcement entities that have users’ footage, and no policies that prohibit law enforcement officers from keeping Ring users’ footage forever.”
#article#full article#bolding mine#amazon#ring#police#police surveillance#ring camera#surveillance state#government surveillance#information security
43 notes
·
View notes
Text

BTSARMY Security Awareness Edition
Securing Mobile Devices Part 1: Identifying Fake Apps (with Mister World Wide Handsome Kim Seokjin)
Contributors:
ddaengsec
emandro1d
ArmyCompsci
Devika��
btsarmysafety
ManelleBTS
#bts#btsarmy#bts jin#kim seokjin#cybersecurity#security#securityawareness#infosec#mobile security#mobile hacking#security awareness training#infographic#information security#malware#adware#malvertising#bloatware#apple ios#android#cell phones
11 notes
·
View notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Text
So y’all wanted more rants about information security & data privacy? Let’s talk about the two main privacy paradigms that are currently competing for dominance in Big Tech. For the sake of not writing a full goddamn thesis I’m going to only talk about models that actually address user privacy (so NOT Facebook’s “privacy is no longer a social norm” bullshit), and only in the context of the USA with a light dip into GDPR.
Very broadly speaking, Big Tech in the US is coalescing into two camps regarding privacy: “opt-out privacy” and “opt-in privacy”. Apple is the flagship and main driver for the concept of “opt-out privacy”. Over the last few years, they’ve leaned heavily into the idea that data should be kept private by default, and only shared under limited circumstances at the user’s request. In other words, the user has privacy by default, and must opt out of that default for data to be shared.
Google is likewise the flagship and main driver for “opt-in privacy”: the idea that data should be shared broadly for the benefit of both the user and the service provider, and sharing is restricted on a case-by-case basis at the user’s request. In other words, the user shares data by default, and must opt in to privacy where desired.
It’s not a coincidence that Apple and Google are the leading drivers for Big Tech’s privacy models. Mobile phones are the most personal devices most people own: your phone goes with you everywhere, and on average, most people check their phones 344 times(!) per day. If you’re like roughly half of US mobile users, you have at least one personal health app on your phone. And until very recently, nobody was stopping shady advertising companies from harvesting every drop of user data they could from people’s phones. All this has made mobile phones one of the primary battlegrounds for digital privacy.
Let’s look at Apple’s model first.
(cut because this is 2k words and I don’t want to murder anyone’s dashes)
You’ve probably seen at least one variation of the recent iPhone privacy ads:

And you’ve probably heard about all the features Apple has been introducing on iOS and the App Store to improve users’ control over who accesses their data, when, and why. Apple is going all-in on the idea that data sharing of any kind should be the exception, not the rule. They appear to be actively working to gut the advertising industry by methodically removing or blocking the mechanisms advertisers use to track users.
Apple can afford to do this for a couple of reasons. First, they make the vast majority of their money by selling hardware, not data-fueled ads. While they do have an advertising business, according to Apple’s own privacy policy, “Apple’s advertising platform does not track you, [...] and does not share user or device data with data brokers.” They admit they do still perform some targeting, but claim they only do so if the targeted group contains more than 5,000 members - which is at least way better than Facebook’s ability to target a single person.
This gets into the second reason why they can afford to gut the broader ads industry: Apple has a wealth of first-party targeting data (I’ll explain what that means in a minute), meaning that not only do they not need other advertisers or data brokers, but also that they’re in direct competition with those other advertisers and data brokers. So going all-in on privacy is good for Apple’s bottom line both from a user value perspective, and from a competitive one.
Now let’s look at Google’s model. If you open your Google account, right on the first page of account management are two sets of privacy settings:
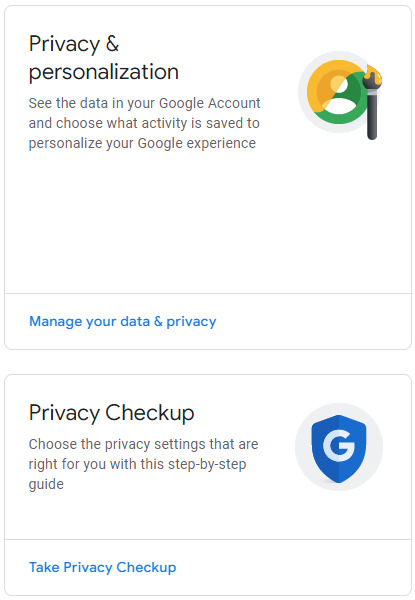
Note the language used: “personalize your Google experience” and “choose the privacy settings that are right for you”. Google has two reasons to collect your data which are mostly tangential to each other. The first and most obvious is that Google-the-advertising-company needs your data in order to more effectively sell ads to third parties. This is what most people think of when they think about Google and privacy: Google wants user data to sell for profit. And, well, yes. Google has built its empire on the back of its ads business, and ads pay for pretty much everything else Google does. Google needs to be able to sell ads to keep funding all the legitimately cool shit it’s doing.
Speaking of legitimately cool shit: Google-the-tech-company’s longest-standing desire has been to create the Star Trek computer in real life: a virtual assistant that “understands you, and [...] can have a conversation with you.” (That’s not just journalism speculation, either - it was explicitly the goal told by Larry & Sergei to employees when I worked at Google.) This is the second reason why Google needs your data: so it can be your own personal Star Trek AI assistant. As anyone who’s worked in an executive assistant role will tell you, you can’t provide useful assistance without having access to just about every component of your employer’s life. Similarly, if you let Google have access to your personal data, it can do a lot of genuinely useful things.
This is why Google’s stance on privacy is so focused on choice: they’re trying to thread the needle between “if you give us your data, we can honestly improve your life” and “if you give us your data, we’ll sell it to third-party advertisers who do all kinds of unpleasant things with it”. The way they’ve internally resolved that ethical conflict is by believing - and trying to convince everyone else - that allowing them to sell your data for profit is a choice you willingly make in order to gain the benefits of Google’s technology.
You can also see the split between opt-in and opt-out privacy in the two most influential laws regulating privacy and the use of user data. The California Consumer Privacy Act (CCPA), as currently enforced, uses the opt-in model: CA residents have the option to stop the sale of their personal data, but the law assumes that user data will be sold unless and until the user chooses otherwise. The CCPA even uses language similar to Google’s: on their website, they say the CCPA “gives consumers more control” over the collection, use, and sale of their data.
The EU’s General Data Protection Regulation (GDPR), on the other hand, primarily uses the opt-out model. This reflects the EU’s stance that privacy is a basic human right, as codified in the 1950 European Convention on Human Rights. The GDPR holds that personal data may not be processed unless there is legal basis to do so, sets strict limits on what constitutes a “legal basis”, and requires companies to collect and use only the minimum amount of data required to fulfil the given legal basis.
While the CCPA and the GDPR use opposite privacy models, the two of them combined with Apple’s insanely effective efforts to stamp out data harvesting (as well as another effort I haven’t talked about at all, which is the death of the cookie) are having an interesting effect on the entire advertising industry. To explain this, I need to sidetrack briefly into what I mean when I say “the advertising industry”.
Most people think of Google and Facebook when they think of advertisers. And, yeah, those are two of the biggest ad-space sellers in the world - but there’s a lot more to the industry. Data brokers like Acxiom, Epsilon, and Oracle America are among the thousands of companies who buy and sell the user data that allows Google and Facebook to effectively sell targeted ad space. The reason you’ve probably never heard of them, however, is because (for the most part) they aren’t the ones who collect the data in the first place.
To vastly oversimplify a stupidly complex industry, you essentially have two types of data brokers: first-party and third-party (with the user themselves being the second party). First-party entities are the ones that collect user data directly for their own purposes; third-party entities buy data from first parties and sell it to other third parties. One company can be both a first- and a third-party entity depending on the situation. For example, Facebook collects your data as a first-party entity, and sells it to a third-party marketing company (let’s say Acxiom). Acxiom combines Facebook’s data with data it’s purchased from other first- and third-party companies and uses it to sell ads. Amazon collects your data as well, making it a first-party entity on its own website. But if Amazon buys Acxiom’s datasets, Amazon becomes a third-party entity for that data. (Cookies are part of this whole data collection and usage ecosystem, but how they work is another entire essay.)
Where the fuck am I going with all this? Back to CCPA, GDPR, and Apple. While they’re all going about it in different ways, the end result is turning out to be the same: a noose around the neck of third-party advertising. If companies are allowed to collect user data for their own legal purposes, but not sell it, then suddenly all those third-party entities become irrelevant and having first-party data is critical. This is what I meant earlier when I said Apple has access to a wealth of first-party data for its own ads business. Apple doesn’t need to sell user data because it makes money from hardware sales, and it doesn’t need to buy user data because it has its own.
Google also has huge amounts of first-party data, but the difference between them and Apple is that Google makes the vast majority of its revenue from selling ads, which depend in part on all that juicy third-party data. Honestly Google is probably going to be okay here still; they have enough else going for them (including their move into hardware sales via the Pixel) that the loss of revenue from selling user data to advertisers won’t hurt them much. But companies who rely entirely on advertising and the sale of user data, like Facebook, will and already do see a huge revenue impact from the move to restrict access to user data.
So what does all this mean for you, the user whose data is in question?
It’s too soon to say for sure, but the good news is that it looks like Apple’s moves are forcing Google to shift further toward opt-out privacy than Google might otherwise have preferred. And for the vast majority of companies, it’s more cost-effective to comply with the various existing and incoming US privacy laws (including CCPA) by using GDPR as a baseline - meaning opt-out privacy may soon be the de facto standard.
This doesn’t mean all companies are actually going to comply in good faith, or at all - already reports are showing “loopholes, bypasses, and outright violations” of Apple’s measures; and GDPR enforcement, especially against Silicon Valley, is painfully low. But privacy industry experts generally agree that the trend is toward stronger protection for users against the unwanted use and sharing of personal information.
As a user, you can help this trend along by actively enforcing your privacy rights wherever you can. If you’re in the EU, take advantage of the GDPR and file complaints against non-compliant companies. If you live in California, exercise your CCPA rights by digging through the privacy policies and settings of your accounts until you find the “do not sell my personal data” toggle. Whether you have an iPhone or an Android, go through your device’s settings and enable every privacy protection measure you can. Likewise, if you have a Google account, take five minutes to go through their privacy checkup feature. It’s actually quite well done, and will give you a better idea of what Google is collecting about you.
The more of us who do this, the stronger the signal we send to both Big Tech and legislators that we want these protections and we will use these protections if we have them. For too long, companies (like Facebook) have argued that users don’t really want privacy - but they’re dead wrong. We just have to prove it to them.
1K notes
·
View notes
Text
Microsoft Windows software and machines behave as if they were natively designed to leak information into negative dimensions.
1 note
·
View note
Text
I guess while we were slacking off during the holiday, some chose to pick up the slack. No pun intended. 😆
5 notes
·
View notes
Text
Look
I just
major mistakes so far in this part of this sequence:
sole survivors are not intrinsically above suspicion
contrariwise, if the sole survivor doesn’t want to be brought along back to the place that just almost killed them, let them stay behind (supervised, of course; see previous point)
if your opponent is (or controls) an ai, NEVER attempt a direct data download. ideally you would never allow two electronic systems to interact without a wholly biological intermediary
likewise, do not mention your objectives, methods, subterfuges, etc. in places not confirmed to be secure from listening devices
#waffle watches#star trek discovery#star trek#i think i need to find something else to watch as a break after this episode#think a little harder#information security#is priority one in these kinds of situations#honestly i'm kind of surprised they held out so well against the klingons last season
6 notes
·
View notes
Text
ascii Hacker - digital artwork 2022

#hacker#digital art#ascii art#hackers#cybersecurity#hacking#infosec#information security#fightmilk22#art#canvapro
2 notes
·
View notes
Text
6 notes
·
View notes
Text
Journey Into Cyber Universe
It's needless to say that how astonishingly advancements are taking place in Cyber and Artificial Intelligence world. The last year the technological revolution has been made by ChatGPT and the world has not been the same. According to my expertise it will revolutionize the world in every aspect of life as we know. It will be very convenient for humans to adapt and utilize this in a very effective way. Obviously there are Pros and Cons to everything and it solely depends what is the intentions and motive of the individual entity. It will be inconvenient for the authorities to prove which one is guilty or otherwise. They have to test the evidence by tools and softwares which can verify that the source is authentic or faked by someone. That's when the role of Information Security comes in. It's absolutely essential now a days to have almost perfect way of securing, monitoring the data of all the people in the world. There are forensics expert in the world who are paid enormously to just found out who bypass the security and know there every tiny details. Cyber Security is still hot and remain like this in further future because the systems are not going anywhere, indeed they are getting much more complex and advanced. The deployment of Cloud makes everything secure and easily available but it has also make it very easy for the ill intentioned people to do there dirty work. So the world is evolving and it's not going to pause or even slow a bit. It's going like a speed of light but in my opinion way more than that if you analyze the history of Earth since Hadean era. In conclusion we need more and more younger talent in this advancing field. That's my erudition on this subject which I have burning passion about.
Thanks
EcStatiX
1 note
·
View note