#OpenShift Platform
Text
How to deploy web application in openshift command line
To deploy a web application in OpenShift using the command-line interface (CLI), follow these steps:
Create a new project: Before deploying your application, you need to create a new project. You can do this using the oc new-project command. For example, to create a project named “myproject”, run the following command:javascriptCopy codeoc new-project myproject
Create an application: Use the oc…

View On WordPress
#openshift openshift4 redhatopenshift openshifttutorial openshiftonline#application deployment#deploy openshift web application using openshift cli command line red hat openshift#kubernetes#openshift#openshift container platform#openshift deploy spring boot jar#openshift installation#openshift login#openshift online#openshift openshift 4 red hat openshift#openshift openshift 4 red hat openshift container platform#openshift tutorial#Openshift webconsole#red hat#red hat openshift#redhat openshift online#web application openshift online
0 notes
Text
CLOUD COMPUTING: A CONCEPT OF NEW ERA FOR DATA SCIENCE
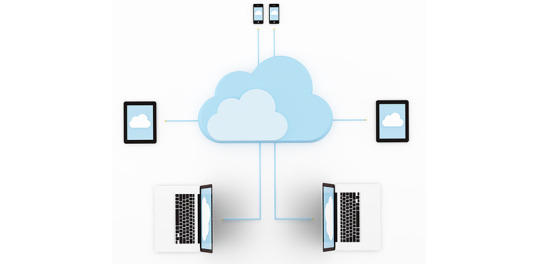
Cloud Computing is the most interesting and evolving topic in computing in the recent decade. The concept of storing data or accessing software from another computer that you are not aware of seems to be confusing to many users. Most the people/organizations that use cloud computing on their daily basis claim that they do not understand the subject of cloud computing. But the concept of cloud computing is not as confusing as it sounds. Cloud Computing is a type of service where the computer resources are sent over a network. In simple words, the concept of cloud computing can be compared to the electricity supply that we daily use. We do not have to bother how the electricity is made and transported to our houses or we do not have to worry from where the electricity is coming from, all we do is just use it. The ideology behind the cloud computing is also the same: People/organizations can simply use it. This concept is a huge and major development of the decade in computing.
Cloud computing is a service that is provided to the user who can sit in one location and remotely access the data or software or program applications from another location. Usually, this process is done with the use of a web browser over a network i.e., in most cases over the internet. Nowadays browsers and the internet are easily usable on almost all the devices that people are using these days. If the user wants to access a file in his device and does not have the necessary software to access that file, then the user would take the help of cloud computing to access that file with the help of the internet.
Cloud computing provide over hundreds and thousands of services and one of the most used services of cloud computing is the cloud storage. All these services are accessible to the public throughout the globe and they do not require to have the software on their devices. The general public can access and utilize these services from the cloud with the help of the internet. These services will be free to an extent and then later the users will be billed for further usage. Few of the well-known cloud services that are drop box, Sugar Sync, Amazon Cloud Drive, Google Docs etc.
Finally, that the use of cloud services is not guaranteed let it be because of the technical problems or because the services go out of business. The example they have used is about the Mega upload, a service that was banned and closed by the government of U.S and the FBI for their illegal file sharing allegations. And due to this, they had to delete all the files in their storage and due to which the customers cannot get their files back from the storage.
Service Models
Cloud Software as a Service
Use the provider's applications running on a cloud infrastructure
Accessible from various client devices through thin client interface such as a web browser
Consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage
Google Apps, Microsoft Office 365, Petrosoft, Onlive, GT Nexus, Marketo, Casengo, TradeCard, Rally Software, Salesforce, ExactTarget and CallidusCloud
Cloud Platform as a Service
Cloud providers deliver a computing platform, typically including operating system, programming language execution environment, database, and web server
Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers
AWS Elastic Beanstalk, Cloud Foundry, Heroku, Force.com, Engine Yard, Mendix, OpenShift, Google App Engine, AppScale, Windows Azure Cloud Services, OrangeScape and Jelastic.
Cloud Infrastructure as a Service
Cloud provider offers processing, storage, networks, and other fundamental computing resources
Consumer is able to deploy and run arbitrary software, which can include operating systems and applications
Amazon EC2, Google Compute Engine, HP Cloud, Joyent, Linode, NaviSite, Rackspace, Windows Azure, ReadySpace Cloud Services, and Internap Agile
Deployment Models
Private Cloud: Cloud infrastructure is operated solely for an organization
Community Cloud : Shared by several organizations and supports a specific community that has shared concerns
Public Cloud: Cloud infrastructure is made available to the general public
Hybrid Cloud: Cloud infrastructure is a composition of two or more clouds
Advantages of Cloud Computing
• Improved performance
• Better performance for large programs
• Unlimited storage capacity and computing power
• Reduced software costs
• Universal document access
• Just computer with internet connection is required
• Instant software updates
• No need to pay for or download an upgrade
Disadvantages of Cloud Computing
• Requires a constant Internet connection
• Does not work well with low-speed connections
• Even with a fast connection, web-based applications can sometimes be slower than accessing a similar software program on your desktop PC
• Everything about the program, from the interface to the current document, has to be sent back and forth from your computer to the computers in the cloud
About Rang Technologies:
Headquartered in New Jersey, Rang Technologies has dedicated over a decade delivering innovative solutions and best talent to help businesses get the most out of the latest technologies in their digital transformation journey. Read More...
#CloudComputing#CloudTech#HybridCloud#ArtificialIntelligence#MachineLearning#Rangtechnologies#Ranghealthcare#Ranglifesciences
8 notes
·
View notes
Text
Paas
Platform as a service (PaaS) : a cloud computing model which allows user to deliver applications over the Internet. In a this model, a cloud provider provides hardware ( like IaaS ) as well as software tools which are usually needed for development of required Application to its users. The hardware and software tools are provided as a Service.
PaaS provides us : OS , Runtime as well as middleware alongside benefits of IaaS. Thus PaaS frees users from maintaining these aspects of application and focus on development of the core app only.
Why choose PaaS :
Increase deployment speed & agility
Reduce length & complexity of app lifecycle
Prevent loss in revenue
Automate provisioning, management, and auto-scaling of applications and services on IaaS platform
Support continuous delivery
Reduce infrastructure operation costs
Automation of admin tasks
The Key Benefits of PaaS for Developers.
There’s no need to focus on provisioning, managing, or monitoring the compute, storage, network and software
Developers can create working prototypes in a matter of minutes.
Developers can create new versions or deploy new code more rapidly
Developers can self-assemble services to create integrated applications.
Developers can scale applications more elastically by starting more instances.
Developers don’t have to worry about underlying operating system and middleware security patches.
Developers can mitigate backup and recovery strategies, assuming the PaaS takes care of this.
conclusion
Common PaaS opensource distributions include CloudFoundry and Redhat OpenShift. Common PaaS vendors include Salesforce’s Force.com , IBM Bluemix , HP Helion , Pivotal Cloudfoundry . PaaS platforms for software development and management include Appear IQ, Mendix, Amazon Web Services (AWS) Elastic Beanstalk, Google App Engine and Heroku.
1 note
·
View note
Text
Red Hat OpenShift API Management
Red Hat open shift:

Red Hat OpenShift is a powerful and popular containerization solution that simplifies the process of building, deploying, and managing containerized applications. Red Hat open shift containers & Kubernetes have become the chief enterprise Kubernetes programs available to businesses looking for a hybrid cloud framework to create highly efficient programs. We are expanding on that by introducing Red Hat OpenShift API Management, a service for both Red Hat OpenShift Dedicated and Red Hat OpenShift Service on AWS that would help accelerate time-to-value and lower the cost of building APIs-first microservices applications.
Red Hat’s managed cloud services portfolio includes Red Hat OpenShift API Management, which helps in development rather than establishing the infrastructure required for APIs. Your development and operations team should be focusing on something other than the infrastructure of an API Management Service because it has some advantages for an organisation.
What is Red Hat OpenShift API Management?
OpenShift API Management is an on-demand solution hosted on Red Hat 3scale (API Management), with integrated sign-on authentication provided by Red Hat SSO. Instead of taking responsibility for running an API management solution on a large-scale deployment, it allows organisations to use API management as part of any service that can integrate applications within their organisation.
It is a completely Red Hat-managed solution that handles all API security, developer onboarding, program management, and analysis. It is ideal for companies that have used the 3scale.net SaaS offering and would like to extend to large-scale deployment. Red Hat will give you upgrades, updates, and infrastructure uptime guarantees for your API services or any other open-source solutions you need. Rather than babysitting the API Management infrastructure, your teams can focus on improving applications that will contribute to the business and Amrita technologies will help you.
Benefits of Red Hat OpenShift API Management
With Open API management, you have all the features to run API-first applications and cloud-hosted application development with microservice architecture. These are the API manager, the API cast ,API gateway, and the Red Hat SSO on the highest level. These developers may define APIs, consume existing APIs, or use Open Shift API management. This will allow them to make their APIs accessible so other developers or partners can use them. Finally, they can deploy the APIs in production using this functionality of Open Shift API management.
API analytics
As soon as it is in production, Open Shift API control allows to screen and offer insight into using the APIs. It will assist you in case your APIs are getting used, how they’re getting used, what demand looks like — and even whether the APIs are being abused. Understanding how your API is used is critical to help manipulate site visitors, anticipate provisioning wishes, and understand how your applications and APIs are used. Once more, all of this is right at your fingertips without having to commit employees to standing up or managing the provider and Amrita technologies will provide you all course details.
Single Sign-On -openshift
The addition of Red Hat SSO means organizations can choose to use their systems (custom coding required) or use Red Hat SSO, which is included with Open Shift API Management. (Please note that the SSO example is provided for API management only and is not a complete SSO solution.)Developers do not need administrative privileges. To personally access the API, it’s just there and there. Instead of placing an additional burden on developers, organizations can retain the user’s permissions and permissions.
Red Hat open shift container platform
These services integrate with Red Hat Open Shift Dedicated and Red Hat Open Shift platform Service for AWS, providing essential benefits to all teams deploying applications .The core services are managed by Red Hat, like Open Shift’s other managed services. This can help your organization reduce operating costs while accelerating the creation, deployment, and evaluation of cloud applications in an open hybrid cloud environment.
Streamlined developer experience in open shift
Developers can use the power and simplicity of three-tier API management across the platform. You can quickly develop APIs before serving them to internal and external clients and then publish them as part of your applications and services. It also provides all the features and benefits of using Kubernetes-based containers. Accelerate time to market with a ready-to-use development environment and help you achieve operational excellence through automated measurement and balancing rise.
Conclusion:
Redhat is a powerful solution that eases the management of APIs in environments running open shifts. Due to its integrability aspect, security concern, and developer-oriented features, it is an ideal solution to help firms achieve successful API management in a container-based environment.
0 notes
Text
Red Hat OpenShift on AWS: Modern Cloud Hosting IBM TAS

The industry-leading comprehensive workplace management solution, IBM TRIRIGA Application Suite (TAS), helps businesses effectively manage their facility portfolios and assets throughout the course of their lives. It assists businesses in managing transactions, capital projects, space, facility maintenance, and facility sustainability. It also helps them schedule facility resources, plan strategic facilities, prepare for leasing accounting, and dispose of assets.
AI and data are becoming more and more important tools as businesses modernize their facilities management. AI-infused real-time insights facilitate dynamic space design. By using shared data, tenants may request services, reserve rooms, optimise portfolio size, and improve the effectiveness of capital projects, lease administration, and other operations. IBM TAS is a straightforward, quick, and adaptable modular solution that offers the ideal combination of applications to optimise your construction lifecycle and get you ready for future demands.
Because it addresses the changing demands of contemporary organisations and places a strong emphasis on simplicity and flexibility, the TRIRIGA Application Suite is an appealing option. The complexity of business systems is decreased by streamlining deployment and management procedures via the consolidation of facility management features onto a single platform. TRIRIGA’s flexible deployment options in on-premises, cloud, and hybrid cloud environments support a range of organizational architectures.
More flexibility is provided by the suite’s streamlined licencing mechanism, allowing customers to adjust their use in accordance with needs. The TRIRIGA Application Suite increases efficiency by emphasising a consistent and improved user experience. Through the clear AppPoints licencing architecture, it provides easy expansion into other capabilities, hence promoting innovation and cost-effectiveness in asset management methods.
As TRIRIGA develops further, TAS will be the main product offered for new, significant upgrades. Customers are receiving assistance from IBM and their partners throughout their migrations so they may benefit from new technologies as soon as they are made available on TAS.
We go over the suggested choices for executing IBM TAS on Amazon Web Services (AWS) in this blog article. We go over the architecture and explain how Red Hat, Amazon, and IBM work together to provide a strong basis for executing IBM TAS. IBM also go over the architectural choices to think about, allowing you to choose the one that best suits the requirements of your company.
Three methods for executing IBM TAS on AWS are covered in this article:
TAS on Red Hat OpenShift hosted by the client
TAS on Red Hat OpenShift Service on Amazon (ROSA), hosted by the client
Partners’ TAS Managed Services
TAS on Red Hat OpenShift hosted by a client
With this deployment, clients may use their in-house, highly experienced team members with Red Hat OpenShift knowledge, especially in security-related areas, to help provide strong protection for their environment. Every element of this ecosystem has to be managed by customers, which calls for constant care, upkeep, and resource allocation.
Customers have complete control over the application and infrastructure with this deployment, but they also assume more management responsibilities for both. This solution is still scalable, giving you the freedom to modify resources to meet changing demand and maximise effectiveness.
Red Hat OpenShift and TAS management skills and architectural design of the client determine the environment’s availability and dependability.
The customer’s software update strategy for Red Hat OpenShift and TAS determines the availability of version upgrades and additional features.
Additionally, since the environment is powered by the customer’s AWS account, it deducts from their current AWS Enterprise Discount Plan, which might have some financial advantages.
In the end, this deployment choice requires careful planning and administration to help assure optimum performance and cost-effectiveness even if it offers autonomy and scalability.Image credit to IBM
TAS on ROSA hosted by the client
RedHat Openshift on AWS
The TAS’s customer-hosted Red Hat OpenShift Service on AWS (ROSA) deployment option is designed to make things easier for users to utilise.
By giving Red Hat and AWS staff complete control over the (OpenShift) ROSA cluster lifecycle management, including updates and security hotfixes, this solution lessens the operational burden on the client.
With Red Hat and AWS staff handling platform and infrastructure administration and support, this solution frees users to concentrate on the TAS application.
This method is perfect for clients that want to concentrate on their TAS application as it simplifies administration and frees up customer resources for other important duties.
In addition, the implementation retains scalability, enabling easy resource modifications to meet changing demand levels.
With this solution, the user may manage software lifecycles in accordance with business deadlines and requirements while maintaining complete control over TAS upgrades and distributed versions.
Strong fault-tolerance and high availability safeguards are also offered by the managed portion of the ROSA platform, which is supported by a 99.95% service level agreement. This SLA is intended to meet your needs for platform stability and dependability so that your TAS application may continue to get services without interruption.
In addition, there are certain financial advantages since the environment uses the customer’s current AWS Enterprise Discount Plan (EDP) because it runs within their AWS account. Customers that are concentrating on TAS applications and outsourcing platform maintenance and monitoring to a managed service may find the ROSA deployment option to be an attractive tool.Image credit to IBM
Partners’ TAS Managed Services
Customers may get a customised solution with the TAS Managed Services by Partners option, which relieves them of the hassles involved in managing their TAS setup. This option allows clients to avoid learning Red Hat OpenShift skills since partners are in charge of administering Red Hat OpenShift. When a client uses a fully managed service from the business partner, they are no longer obliged to maintain the platform or application.
By using the deployment’s inherent scalability, this solution enables organisations to concentrate on their primary goals while enabling smooth resource modifications in response to changing demand.
Subject to a SLA with the partner, the business partner is responsible for the environment’s availability, resilience, and dependability.
Customers also depend on partners for TAS version upgrades and new feature availability, which may be contingent on the partner’s schedule and offers.
Customers may only see and access the application endpoints that are necessary for their business activities, and the environment is run inside the partner’s AWS account. The client has to be aware that their data is stored in and managed by the partner AWS account.
Customers looking for a simplified, scalable, and well-supported TAS deployment solution may find the TAS Managed Services by Partners option to be an appealing offer.Image credit to IBM
Note: The architecture shown above is generic. The partner solution may cause variations in the actual architecture.
Concluding remarks
Every deployment option for the IBM TAS has unique benefits and drawbacks. To guarantee an effective and successful IBM TAS implementation, customers should evaluate their infrastructure, customization, internal capabilities, and cost factors. Customers may choose the deployment option that best suits their company goals by being aware of the advantages and disadvantages of each one.
Read more on Govindhtech.com
#AWS#RedHatOpenShift#IBM#IBMTAS#govindhtech#HybridCloud#news#technews#technology#technologytrends#technologynews
0 notes
Text
Red Hat open shift API Management
Red Hat open shift:

Red Hat OpenShift is a powerful and popular containerization solution that simplifies the process of building, deploying, and managing containerized applications. Red Hat open shift containers & Kubernetes have become the chief enterprise Kubernetes programs available to businesses looking for a hybrid cloud framework to create highly efficient programs. We are expanding on that by introducing Red Hat OpenShift API Management, a service for both Red Hat OpenShift Dedicated and Red Hat OpenShift Service on AWS that would help accelerate time-to-value and lower the cost of building APIs-first microservices applications.
Red Hat’s managed cloud services portfolio includes Red Hat OpenShift API Management, which helps in development rather than establishing the infrastructure required for APIs. Your development and operations team should be focusing on something other than the infrastructure of an API Management Service because it has some advantages for an organisation.
What is Red Hat OpenShift API Management?
OpenShift API Management is an on-demand solution hosted on Red Hat 3scale (API Management), with integrated sign-on authentication provided by Red Hat SSO. Instead of taking responsibility for running an API management solution on a large-scale deployment, it allows organisations to use API management as part of any service that can integrate applications within their organisation.
It is a completely Red Hat-managed solution that handles all API security, developer onboarding, program management, and analysis. It is ideal for companies that have used the 3scale.net SaaS offering and would like to extend to large-scale deployment. Red Hat will give you upgrades, updates, and infrastructure uptime guarantees for your API services or any other open-source solutions you need. Rather than babysitting the API Management infrastructure, your teams can focus on improving applications that will contribute to the business and Amrita technologies will help you.
Benefits of Red Hat OpenShift API Management
With Open API management, you have all the features to run API-first applications and cloud-hosted application development with microservice architecture. These are the API manager, the API cast ,API gateway, and the Red Hat SSO on the highest level. These developers may define APIs, consume existing APIs, or use Open Shift API management. This will allow them to make their APIs accessible so other developers or partners can use them. Finally, they can deploy the APIs in production using this functionality of Open Shift API management.
API analytics
As soon as it is in production, Open Shift API control allows to screen and offer insight into using the APIs. It will assist you in case your APIs are getting used, how they’re getting used, what demand looks like — and even whether the APIs are being abused. Understanding how your API is used is critical to help manipulate site visitors, anticipate provisioning wishes, and understand how your applications and APIs are used. Once more, all of this is right at your fingertips without having to commit employees to standing up or managing the provider and Amrita technologies will provide you all course details.
Single Sign-On -openshift
The addition of Red Hat SSO means organizations can choose to use their systems (custom coding required) or use Red Hat SSO, which is included with Open Shift API Management. (Please note that the SSO example is provided for API management only and is not a complete SSO solution.)Developers do not need administrative privileges. To personally access the API, it’s just there and there. Instead of placing an additional burden on developers, organizations can retain the user’s permissions and permissions.
Red Hat open shift container platform
These services integrate with Red Hat Open Shift Dedicated and Red Hat Open Shift platform Service for AWS, providing essential benefits to all teams deploying applications .The core services are managed by Red Hat, like Open Shift’s other managed services. This can help your organization reduce operating costs while accelerating the creation, deployment, and evaluation of cloud applications in an open hybrid cloud environment.
Streamlined developer experience in open shift
Developers can use the power and simplicity of three-tier API management across the platform. You can quickly develop APIs before serving them to internal and external clients and then publish them as part of your applications and services. It also provides all the features and benefits of using Kubernetes-based containers. Accelerate time to market with a ready-to-use development environment and help you achieve operational excellence through automated measurement and balancing rise.
Conclusion:
Redhat is a powerful solution that eases the management of APIs in environments running open shifts. Due to its integrability aspect, security concern, and developer-oriented features, it is an ideal solution to help firms achieve successful API management in a container-based environment.
0 notes
Text
How One Chinese Company is Streamlining Orders with AI Assistance from IBM
<h1>How One Company is Using AI to Streamline its Operations</h1>
<p>Yuanfeng Automotive is a major supplier of car parts. They have 9 research centers and over 240 factories around the world, supplying auto manufacturers with components for vehicles. Every day they receive lots of orders from car companies and other factories that buy from them.</p>
<p>Previously, processing all these orders was a very manual task. Two employees at each plant would spend over 2 and a half hours each day sorting the orders by hand. Unfortunately, they made mistakes about 15% of the time. This slow, error-prone process was costing the company time and money.</p>
<p>This year, Yuanfeng decided to use artificial intelligence (AI) to help solve this problem. They used a type of AI called IBM Watson Discovery. This AI is really good at understanding complicated business documents and figuring out patterns. Yuanfeng trained it to automatically sort their general orders into specific internal orders for each factory.</p>
<p>Now, the AI handles the entire order sorting process without any human involvement. It works much faster and more accurately than people, reducing mistakes to just 3% of orders. This AI system has significantly cut costs and increased efficiency for Yuanfeng.</p>
<h2>Partnering with IBM on AI Solutions</h2>
<p>Yuanfeng worked with IBM to create this AI application. Mr. Zhu Hui, general manager at IBM, highlights it as an example of how IBM helps manufacturers become smarter with technology. IBM believes that combining cloud computing and AI is key for transforming businesses digitally.</p>
<p>As Mr. Miao Kaiyuan, head of IBM in China, explains: "We want to walk alongside our customers on this journey of change. Our goal is to take technological know-how and make it useful for improving business results." This year, IBM China focused on serving existing clients well while also exploring new opportunities.</p>
<h2>AI Driving Strong Growth for IBM in China</h2>
<p>In the last quarter, IBM's global revenue topped $141 billion - a 15% increase. Revenue from hybrid cloud services rose even faster at 20% compared to last year. Mr. Miao attributes this success to IBM's strategy of hybrid cloud and AI meeting real business needs.</p>
<p>Mr. Chen Guohao from IBM explains how the company integrates AI throughout its software, hardware, and services for Chinese customers. Key products include the Red Hat OpenShift platform, Cloud Paks with built-in AI, and solutions tailored for specific industries. Chinese companies in fields like manufacturing, automotive, energy and finance are using IBM's technologies to automate processes and gain valuable insights.</p>
<p>"Our goal is to be a trustworthy partner that helps clients advance their business through innovation," Mr. Miao concludes. "Together with customers, we aim to apply technology for the greater good."</p>
<p>With IBM continuing to foster strong partnerships in China, the future looks bright for how AI will transform operations across many industries. Effective collaboration between technology providers and businesses will remain crucial.
0 notes
Text
Mastering Digital Transformation: OpenShift Migration Unveiled
In the fast-paced world of digital transformation, OpenShift migration has emerged as a beacon for organizations seeking to reshape their technological landscape. As businesses recognize the imperative of adaptability and scalability, OpenShift migration becomes a pivotal strategy to harness the power of container orchestration. In this comprehensive article, we will delve into the nuances of OpenShift migration, exploring key steps and highlighting the diverse benefits it bestows upon enterprises.
Decoding OpenShift Migration: A Strategic Evolution
Core Concept of OpenShift Migration:
At its essence, OpenShift migration involves the strategic transition of applications from traditional on-premises environments or alternative container platforms to the OpenShift container orchestration framework. This strategic shift is aimed at propelling organizations towards heightened efficiency, streamlined workflows, and unparalleled flexibility in adapting to modern IT demands.
Navigating the Migration Landscape:
Strategic Assessment and Tactical Planning: The journey commences with a meticulous assessment of existing applications, infrastructure, and dependencies. This phase is pivotal for discerning potential challenges and crafting a comprehensive migration plan. Factors like application interdependencies, data storage intricacies, and robust security protocols come under scrutiny.
Artistry of Containerization: The heart of OpenShift migration lies in the meticulous art of containerization. Applications are encapsulated into containers, ensuring seamless portability across diverse environments. The inherent compatibility with Docker containers adds an extra layer of versatility, facilitating a smooth and adaptable transition.
Precision in Migration Execution: The migration plan unfolds with precision, aiming to minimize downtime and disruptions. Organizations may opt for a phased approach or migrate applications sequentially, strategically navigating dependencies and prioritizing critical components for a seamless transition.
Harmonious Integration and Precision Optimization: Post-migration, the focus shifts to seamlessly integrating applications with OpenShift's rich feature set. Monitoring, logging, and scaling capabilities are harnessed for optimal performance. This phase becomes an opportune moment to implement optimization measures, amplifying the benefits of the newly embraced containerized environment.
Validation through Rigorous Testing: Rigorous testing becomes the litmus test for the success of migration efforts. Functional, performance, and security testing ensure that applications seamlessly adapt to the OpenShift environment, delivering on the promised efficiency and scalability without compromising on reliability.
Vigilant Monitoring and Iterative Refinement: Robust monitoring tools are employed to keep a vigilant eye on application performance and resource utilization. Continuous improvement initiatives are seamlessly integrated, allowing organizations to refine their OpenShift deployment based on real-world insights and user feedback.
Elevating Operations: The Varied Merits of OpenShift Migration
Seamless Scalability: OpenShift empowers businesses to scale applications effortlessly, adapting to dynamic workloads and optimizing resource usage without sacrificing performance.
Automated Efficiency: The robust automation features within OpenShift streamline deployment processes, minimizing manual intervention, and significantly reducing the risk of errors, fostering a more efficient operational landscape.
Freedom of Infrastructure Choice: OpenShift's inherent compatibility with various cloud providers and on-premises environments provides businesses with the freedom to choose infrastructure tailored to their specific needs, fostering a sense of control over the technological landscape.
In conclusion, OpenShift migration isn't merely a technological shift; it's a strategic evolution propelling organizations toward a future where agility and scalability are paramount. By meticulously following a well-crafted migration process and leveraging the multifaceted capabilities of OpenShift, organizations position themselves at the forefront of the digital revolution, ready to thrive in the ever-shifting landscape of technology.
0 notes
Text
How to deploy web application in openshift web console
To deploy a web application in OpenShift using the web console, follow these steps:
Create a new project: Before deploying your application, you need to create a new project. You can do this by navigating to the OpenShift web console, selecting the “Projects” dropdown menu, and then clicking on “Create Project”. Enter a name for your project and click “Create”.
Add a new application: In the…

View On WordPress
#openshift openshift4 redhatopenshift deploywebapplication openshiftonline deploy web application in openshift web console#application deployment#Deploy application in openshift#deploy application openshift#openshift#openshift 4#openshift container platform#openshift deploy java application#openshift deploy spring boot jar#openshift for beginners#openshift online cluster#openshift tutorial#Openshift webconsole#red hat#red hat openshift#red hat openshift webconsole#redhat openshift online#web application openshift online
0 notes
Text
Identity Security
In today's digitized world, where everything from shopping to banking is conducted online, ensuring identity security has become paramount. With cyber threats rising, protecting our personal information from unauthorized access has become more critical than ever. This blog post will delve into identity security, its significance, and practical steps to safeguard your digital footprint.
youtube
Identity security is the measures taken to protect personal information from being accessed, shared, or misused without authorization. It encompasses a range of practices designed to safeguard one's identity, such as securing online accounts, protecting passwords, and practicing safe online browsing habits.
Maintaining robust identity security is crucial for several reasons. Firstly, it helps prevent identity theft, which can have severe consequences, including financial loss, damage to one's credit score, and emotional distress. Secondly, identity security safeguards personal privacy by ensuring that sensitive information remains confidential. Lastly, it helps build trust in online platforms and e-commerce, enabling users to transact confidently.
Table of Contents
Identity Security
Back to basics: Identity Security
Example: Identity Security: The Workflow
Starting Zero Trust Identity Management
Challenges to zero trust identity management
Knowledge Check: Multi-factor authentication (MFA)
The Move For Zero Trust Authentication
Considerations for zero trust authentication
The first action is to protect Identities.
Adopting Zero Trust Authentication
Zero trust authentication: Technology with risk-based authentication
Conditional Access
Zero trust authentication: Technology with JIT techniques
Final Notes For Identity Security
Zero Trust Identity: Validate Every Device
Quick Links
Contact
Subscribe Now
Highlights: Identity Security
Sophisticated Attacks
Identity security has pushed authentication to a new, more secure landscape, reacting to improved technologies and sophisticated attacks. The need for more accessible and secure authentication has led to the wide adoption of zero-trust identity management zero trust authentication technologies like risk-based authentication (RBA), fast identity online (FIDO2), and just-in-time (JIT) techniques.
New Attack Surface
If you examine our identities, applications, and devices, they are in the crosshairs of bad actors, making them probable threat vectors. In addition, we are challenged by the sophistication of our infrastructure, which increases our attack surface and creates gaps in our visibility. Controlling access and the holes created by complexity is the basis of all healthy security. Before we jump into the zero-trust authentication and components needed to adopt zero-trust identity management, let’s start with the basics of identity security.
Related: Before you proceed, you may find the following posts helpful
SASE Model
Zero Trust Security Strategy
Zero Trust Network Design
OpenShift Security Best Practices
Zero Trust Networking
Zero Trust Network
Zero Trust Access
Zero Trust Identity
Key Identity Security Discussion Points:
Introduction to identity security and what is involved.
Highlighting the details of the challenging landscape along with recent trends.
Technical details on how to approach implementing a zero trust identity strategy.
Scenario: Different types of components make up zero trust authentication management.
Details on starting a zero trust identity security project.
Back to basics: Identity Security
In its simplest terms, an identity is an account or a persona that can interact with a system or application. And we can have different types of identities.
Human Identity: Human identities are the most common. These identities could be users, customers, or other stakeholders requiring various access levels to computers, networks, cloud applications, smartphones, routers, servers, controllers, sensors, etc.
Non-Human: Identities are also non-human as operations automate more processes. These types of identities are seen in more recent cloud-native environments. Applications and microservices use these machine identities for API access, communication, and the CI/CD tools.
♦Tips for Ensuring Identity Security:
1. Strong Passwords: Create unique, complex passwords for all your online accounts. Passwords should contain a combination of upper- and lowercase letters, numbers, and special characters. Do not use easily guessable information, such as birthdates or pet names.
2. Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring an additional verification step, such as a temporary code sent to your phone or email.
3. Keep Software Up to Date: Regularly update your operating system, antivirus software, and other applications. These updates often include security patches that address known vulnerabilities.
4. Be Cautious with Personal Information: Be mindful of the information you share online. Avoid posting sensitive details on public platforms or unsecured websites, such as your full address or social security number.
5. Secure Wi-Fi Networks: When connecting to public Wi-Fi networks, ensure they are secure and encrypted. Avoid accessing sensitive information, such as online banking, on public networks.
6. Regularly Monitor Accounts: Keep a close eye on your financial accounts, credit reports, and other online platforms where personal information is stored. Report any suspicious activity immediately.
7. Use Secure Websites: Look for the padlock symbol and “https” in the website address when providing personal information or making online transactions. This indicates that the connection is secure and encrypted.
Example: Identity Security: The Workflow
The concept of identity security is straightforward and follows a standard workflow that can be understood and secured. First, a user logs into their employee desktop and is authenticated as an individual who should have access to this network segment. This is the authentication stage.
They have appropriate permissions assigned so they can navigate to the required assets (such as an application or file servers) and are authorized as someone who should have access to this application. This is the authorization stage.
As they move across the network to carry out their day-to-day duties, all of this movement is logged, and all access information is captured and analyzed for auditing purposes. Anything outside of normal behavior is flagged. Splunk UEBA has good features here.Diagram: Identity security workflow.
Identity Security: Stage of Authentication
Authentication: You need to authenticate every human and non-human identity accurately. After an identity is authenticated to confirm who it is, it only gets a free one for some to access the system with impunity.
Identity Security: Stage of Re-Authentication
Identities should be re-authenticated if the system detects suspicious behavior or before completing tasks and accessing data that is deemed to be highly sensitive. If we have an identity that acts outside of normal baseline behavior, they must re-authenticate.
Identity Security: Stage of Authorization
Then we need to move to the authorization: It’s necessary to authorize the user to ensure they’re allowed access to the asset only when required and only with the permissions they need to do their job. So we have authorized each identity on the network with the proper permissions so they can access what they need and not more.
Identity Security: Stage of Access
Then we look into the Access: Provide access for that identity to authorized assets in a structured manner. How can the appropriate access be given to the person/user/device/bot/script/account and nothing more? Following the practices of zero trust identity management and least privilege. Ideally, access is granted to microsegments instead of significant VLANs based on traditional zone-based networking.
Identity Security: Stage of Audit
Finally, Audit: All identity activity must be audited or accounted for. Auditing allows insight and evidence that Identity Security policies are working as intended. How do you monitor the activities of identities? How do you reconstruct and analyze the actions an identity performed?
An auditing capability ensures visibility into activities performed by an identity, provides context for the identity’s usage and behavior, and enables analytics that identify risk and provide insights to make smarter decisions about access.
Starting Zero Trust Identity Management
Now, we have an identity as the new perimeter compounded by identity being the new target. Any identity is a target. Looking at the modern enterprise landscape, it’s easy to see why. Every employee has multiple identities and uses several devices.
What makes this worse is that security teams’ primary issue is that identity-driven attacks are hard to detect. For example, how do you know if a bad actor or a sys admin uses the privilege controls? As a result, security teams must find a reliable way to monitor suspicious user behavior to determine the signs of compromised identities.
We now have identity sprawl,, which may be acceptable if only one of those identities has user access. However, they don’t, and they most likely have privileged access. All these widen the attack surface by creating additional human and machine identities that can gain privileged access under certain conditions. All of which will establish new pathways for bad actors.
We must adopt a different approach to secure our identities regardless of where they may be. Here, we can look for a zero-trust identity management approach based on identity security. Next, I’d like to discuss your common challenges when adopting identity security.Diagram: Zero trust identity management. The challenges.
Challenges to zero trust identity management
Challenge: Zero trust identity management and privilege credential compromise
Current environments may result in anonymous access to privileged accounts and sensitive information. Unsurprisingly, 80% of breaches start with compromised privilege credentials. If left unsecured, attackers can compromise these valuable secrets and credentials to gain possession of privileged accounts and perform advanced attacks or use them to exfiltrate data.
Challenge: Zero trust identity management and exploiting privileged accounts
So, we have two types of bad actors. First, there are external attackers and malicious insiders that can exploit privileged accounts to orchestrate a variety of attacks. Privileged accounts are used in nearly every cyber attack. With privileged access, bad actors can disable systems, take control of IT infrastructure, and gain access to sensitive data. So, we face several challenges when securing identities, namely protecting, controlling, and monitoring privileged access.
Challenge: Zero trust identity management and lateral movements
Lateral movements will happen. A bad actor has to move throughout the network. They will never land directly on a database or important file server. The initial entry point into the network could be an unsecured IoT device, which does not hold sensitive data. As a result, bad actors need to pivot across the network.
They will laterally move throughout the network with these privileged accounts, looking for high-value targets. They then use their elevated privileges to steal confidential information and exfiltrate data. There are many ways to exfiltrate data, with DNS being a common vector that often goes unmonitored. How do you know a bad actor is moving laterally with admin credentials using admin tools built into standard Windows desktops?
Challenge: Zero trust identity management and distributed attacks
These attacks are distributed, and there will be many dots to connect to understand threats on the network. Could you look at ransomware? Enrolling the malware needs elevated privilege, and it’s better to detect this before the encryption starts. Some ransomware families perform partial encryption quickly. Once encryption starts, it’s game over. You need to detect this early in the kill chain in the detect phase.
The best way to approach zero trust authentication is to know who accesses the data, ensure the users they claim to be, and operate on the trusted endpoint that meets compliance. There are plenty of ways to authenticate to the network; many claim password-based authentication is weak.
The core of identity security is understanding that passwords can be phished; essentially, using a password is sharing. So, we need to add multifactor authentication (MFA). MFA gives a big lift but needs to be done well. You can get breached even if you have an MFA solution in place.
Knowledge Check: Multi-factor authentication (MFA)
More than simple passwords are needed for healthy security. A password is a single authentication factor – anyone with it can use it. No matter how strong it is, keeping information private is useless if lost or stolen. You must use a different secondary authentication factor to secure your data appropriately.
Here’s a quick breakdown:
•Two-factor authentication: This method uses two-factor classes to provide authentication. It is also known as ‘2FA’ and ‘TFA.’
•Multi-factor authentication: use of two or more factor classes to provide authentication. This is also represented as ‘MFA.’
•Two-step verification: This method of authentication involves two independent steps but does not necessarily require two separate factor classes. It is also known as ‘2SV’.
•Strong authentication: authentication beyond simply a password. It may be represented by the usage of ‘security questions’ or layered security like two-factor authentication.
The Move For Zero Trust Authentication
No MFA solution is an island. Every MFA solution is just one part of multiple components, relationships, and dependencies. Each piece is an additional area where an exploitable vulnerability can occur.
Essentially, any component in the MFA’s life cycle, from provisioning to de-provisioning and everything in between, is subject to exploitable vulnerabilities and hacking. And like the proverbial chain, it’s only as strong as its weakest link.
The need for zero trust authentication: Two or More Hacking Methods Used
Many MFA attacks use two or more of the leading hacking methods. Often, social engineering is used to start the attack and get the victim to click on a link or to activate a process, which then uses one of the other methods to accomplish the necessary technical hacking.
For example, a user gets a phishing email directing them to a fake website, which accomplishes a man-in-the-middle (MitM) attack and steals credential secrets. Or physical theft of a hardware token is performed, and then the token is forensically examined to find the stored authentication secrets. MFA hacking requires using two or all of these main hacking methods.
You can’t rely on MFA alone; you must validate privileged users with context-aware Adaptive Multifactor Authentication and secure access to business resources with Single Sign-On. Unfortunately, credential theft remains the No. 1 area of risk. And bad actors are getting better at bypassing MFA using a variety of vectors and techniques.
For example, a bad actor can be tricked into accepting a push notification to their smartphone to grant access in the context of getting admission. You are still acceptable to man-in-the-middle attacks. This is why MFA and IDP vendors introduce risk-based authentication and step-up authentication. These techniques limited the attack surface, which we will talk about soon.
Considerations for zero trust authentication
Think like a bad actor.
By thinking like a bad actor, we can attempt to identify suspicious activity, restrict lateral movement, and contain threats. Try envisioning what you would look for if you were a bad external actor or malicious insider. For example, are you looking to steal sensitive data to sell it to competitors, or are you looking to start Ransomware binaries or use your infrastructure for illicit crypto mining?
Attacks with happen
The harsh reality is that attacks will happen, and you can only partially secure some of their applications and infrastructure wherever they exist. So it’s not a matter of ‘if’ but a concern of “when.” Protection from all the various methods that attackers use is virtually impossible, and there will occasionally be day 0 attacks. So, they will get in eventually; It’s all about what they can do once they are in.Diagram: Zero trust authentication. Key considerations.
The first action is to protect Identities.
Therefore, the very first thing you must do is protect their identities and prioritize what matters most – privileged access. Infrastructure and critical data are only fully protected if privileged accounts, credentials, and secrets are secured and protected.
The bad actor needs privileged access.
We know that about 80% of breaches tied to hacking involve using lost or stolen credentials. Compromised identities are the common denominator in virtually every severe attack. The reason is apparent:
The bad actor needs privileged access to the network infrastructure to steal data. However, without privileged access, an attacker is severely limited in what they can do. Furthermore, without privileged access, they may be unable to pivot from one machine to another. And the chances of landing on a high-value target are doubtful.
The malware requires admin access.
The malware used to pivot and requires admin access to gain persistence; privileged access without vigilant management creates an ever-growing attack surface around privileged accounts.
Adopting Zero Trust Authentication
Zero trust authentication: Technology with Fast Identity Online (FIDO2)
Where can you start identity security with all of this? Firstly, we can look at a zero-trust authentication protocol. We need an authentication protocol that can be phishing-resistant. This is FIDO2, known as Fast Identity Online (FIDO2), built on two protocols that effectively remove any blind protocols. FIDO authentication Fast Identity Online (FIDO) is a challenge-response protocol that uses public-key cryptography. Rather than using certificates, it manages keys automatically and beneath the covers.
The FIDO2 standards
FIDO2 uses two standards. The Client to Authenticator Protocol (CTAP) describes how a browser or operating system establishes a connection to a FIDO authenticator. The WebAuthn protocol is built into browsers and provides an API that JavaScript from a web service can use to register a FIDO key, send a challenge to the authenticator, and receive a response to the challenge.
So there is an application the user wants to go to, and then we have the client that is often the system’s browser, but it can be an application that can speak and understand WebAuthn. FIDO provides a secure and convenient way to authenticate users without using passwords, SMS codes, or TOTP authenticator applications. Modern computers and smartphones and most mainstream browsers understand FIDO natively.
FIDO2 addresses phishing by cryptographically proving that the end-user has a physical position over the authentication. There are two types of authenticators: a local authenticator, such as a USB device, and a roaming authenticator, such as a mobile device. These need to be certified FIDO2 vendors.
The other is a platform authenticator such as Touch ID or Windows Hello. While roaming authenticators are available, for most use cases, platform authenticators are sufficient. This makes FIDO an easy, inexpensive way for people to authenticate. The biggest impediment to its widespread use is that people won’t believe something so easy is secure.
Zero trust authentication: Technology with risk-based authentication
Risk is not a static attribute, and it needs to be re-calculated and re-evaluated so you can make intelligent decisions for step-up and user authentication. We have Cisco DUO that reacts to risk-based signals at the point of authentication.
So, these risk signals are processed in real time to detect signs of known account takeout signals. These signals may include Push Bombs, Push Sprays, and Fatigue attacks. Also, a change of location can signal high risk. Risk-based authentication (RBA) is usually coupled with step-up authentication.
For example, let’s say your employees are under attack. RBA can detect this attack as a stuffing attack and move from a classic authentication approach to a more secure verified PUSH approach than the standard PUSH.
This would add more friction but result in better security, such as adding three to six digital display keys at your location/devices, and you need to enter this key in your application. This eliminates fatigue attacks. This verified PUSH approach can be enabled at an enterprise level or just for a group of users.
Conditional Access
Then, we move towards conditional access, a step beyond authentication. Conditional access goes beyond authentication to examine the context and risk of each access attempt. For example, contextual factors may include consecutive login failures, geo-location, type of user account, or device IP to either grant or deny access. Based on those contextual factors, it may be granted only to specific network segments.
A key point: Risk-based decisions and recommended capabilities
The identity security solution should be configurable to allow SSO access, challenge the user with MFA, or block access based on predefined conditions set by policy. It would help if you looked for a solution that can offer a broad range of shapes, such as IP range, day of the week, time of day, time range, device O/S, browser type, country, and user risk level.
These context-based access policies should be enforceable across users, applications, workstations, mobile devices, servers, network devices, and VPNs. A key question is whether the solution makes risk-based access decisions using a behavior profile calculated for each user.
Zero trust authentication: Technology with JIT techniques
Secure privileged access and manage entitlements. For this reason, many enterprises employ a least privilege approach, where access is restricted to the resources necessary for the end-user to complete their job responsibilities with no extra permission. A standard technology here would be Just in Time (JIT). Implementing JIT ensures that identities have only the appropriate privileges, when necessary, as quickly as possible and for the least time required.
JIT techniques that dynamically elevate rights only when needed are a technology to enforce the least privilege. The solution allows for JIT elevation and access on a “by request” basis for a predefined period, with a full audit of privileged activities. Full administrative rights or application-level access can be granted, time-limited, and revoked.
Final Notes For Identity Security
Zero trust identity management is where we continuously verify users and devices to ensure access, and privileges are granted only when needed. The backbone of zero-trust identity security starts by assuming that any human or machine identity with access to your applications and systems may have been compromised.
The “assume breach” mentality requires vigilance and a Zero Trust approach to security centered on securing identities. With identity security as the backbone of a zero-trust process, teams can focus on identifying, isolating, and stopping threats from compromising identities and gaining privilege before they can harm.Diagram: Identity Security: Final notes.
Zero Trust Authentication
The identity-centric focus of zero trust authentication uses an approach to security to ensure that every person and every device granted access is who and what they say they are. It achieves this authentication by focusing on the following key components:
The network is always assumed to be hostile.
External and internal threats always exist on the network.
Network locality needs to be more sufficient for deciding trust in a network. Just so you know, other contextual factors, as discussed, must be taken into account.
Every device, user, and network flow is authenticated and authorized. All of this must be logged.
Security policies must be dynamic and calculated from as many data sources as possible.
Zero Trust Identity: Validate Every Device
Not just the user
Validate every device. While user verification adds a level of security, more is needed. We must ensure that the devices are authenticated and associated with verified users, not just the users.
Risk-based access
Risk-based access intelligence should reduce the attack surface after a device has been validated and verified as belonging to an authorized user. This allows aspects of the security posture of endpoints, like device location, a device certificate, OS, browser, and time, to be used for further access validation.
Device Validation: Reduce the attack surface
Remember that while device validation helps limit the attack surface, device validation is only as reliable as the endpoint’s security. Antivirus software to secure endpoint devices will only get you so far. We need additional tools and mechanisms that can tighten security even further.
Summary: Identity Security
In today’s interconnected digital world, protecting our identities online has become more critical than ever. From personal information to financial data, our digital identities are vulnerable to various threats. This blog post aimed to shed light on the significance of identity security and provide practical tips to enhance your online safety.
Section 1: Understanding Identity Security
Identity security refers to the measures taken to safeguard personal information and prevent unauthorized access. It encompasses protecting sensitive data such as login credentials, financial details, and personal identification information (PII). By ensuring robust identity security, individuals can mitigate the risks of identity theft, fraud, and privacy breaches.
Section 2: Common Threats to Identity Security
In this section, we’ll explore some of the most prevalent threats to identity security. This includes phishing attacks, malware infections, social engineering, and data breaches. Understanding these threats is crucial for recognizing potential vulnerabilities and taking appropriate preventative measures.
Section 3: Best Practices for Strengthening Identity Security
Now that we’ve highlighted the importance of identity security and identified common threats let’s delve into practical tips to fortify your online presence:
1. Strong and Unique Passwords: Utilize complex passwords that incorporate a combination of letters, numbers, and special characters. Avoid using the same password across multiple platforms.
2. Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security. This typically involves a secondary verification method, such as a code sent to your mobile device.
3. Regular Software Updates: Keep all your devices and applications current. Software updates often include security patches that address known vulnerabilities.
4. Beware of Phishing Attempts: Be cautious of suspicious emails, messages, or calls asking for personal information. Verify the authenticity of requests before sharing sensitive data.
5. Secure Wi-Fi Networks: When connecting to public Wi-Fi networks, use a virtual private network (VPN) to encrypt your internet traffic and protect your data from potential eavesdroppers.
Section 4: The Role of Privacy Settings
Privacy settings play a crucial role in controlling the visibility of your personal information. Platforms and applications often provide various options to customize privacy preferences. Take the time to review and adjust these settings according to your comfort level.
Section 5: Monitoring and Detecting Suspicious Activity
Remaining vigilant is paramount in maintaining identity security. Regularly monitor your financial statements, credit reports, and online accounts for any unusual activity. Promptly report any suspicious incidents to the relevant authorities.
Conclusion:
In an era where digital identities are constantly at risk, prioritizing identity security is non-negotiable. By implementing the best practices outlined in this blogpost, you can significantly enhance your online safety and protect your valuable personal information. Remember, proactive measures and staying informed are key to maintaining a secure digital identity.
0 notes
Text
Dell-Red Hat tackle DIY OpenShift deployments with appliance | TechTarget
Dell is expanding its partnership with Red Hat, speeding the deployment and simplifying the management of containers with an appliance that also adds more security and customer control.
Dell Apex Cloud Platform for Red Hat OpenShift builds on a partnership launched in 2022, this time focused on an appliance jointly engineered by the two vendors to combine OpenShift’s container management…
View On WordPress
0 notes
Text
Red Hat OpenShift API Management
Red Hat open shift API Management

Red Hat OpenShift is a powerful and popular containerization solution that simplifies the process of building, deploying, and managing containerized applications. Red Hat open shift containers & Kubernetes have become the chief enterprise Kubernetes programs available to businesses looking for a hybrid cloud framework to create highly efficient programs. We are expanding on that by introducing Red Hat OpenShift API Management, a service for both Red Hat OpenShift Dedicated and Red Hat OpenShift Service on AWS that would help accelerate time-to-value and lower the cost of building APIs-first microservices applications.
Red Hat’s managed cloud services portfolio includes Red Hat OpenShift API Management, which helps in development rather than establishing the infrastructure required for APIs. Your development and operations team should be focusing on something other than the infrastructure of an API Management Service because it has some advantages for an organisation.
What is Red Hat OpenShift API Management?
OpenShift API Management is an on-demand solution hosted on Red Hat 3scale (API Management), with integrated sign-on authentication provided by Red Hat SSO. Instead of taking responsibility for running an API management solution on a large-scale deployment, it allows organisations to use API management as part of any service that can integrate applications within their organisation.
It is a completely Red Hat-managed solution that handles all API security, developer onboarding, program management, and analysis. It is ideal for companies that have used the 3scale.net SaaS offering and would like to extend to large-scale deployment. Red Hat will give you upgrades, updates, and infrastructure uptime guarantees for your API services or any other open-source solutions you need. Rather than babysitting the API Management infrastructure, your teams can focus on improving applications that will contribute to the business and Amrita technologies will help you.
Benefits of Red Hat OpenShift API Management
With Open API management, you have all the features to run API-first applications and cloud-hosted application development with microservice architecture. These are the API manager, the API cast ,API gateway, and the Red Hat SSO on the highest level. These developers may define APIs, consume existing APIs, or use Open Shift API management. This will allow them to make their APIs accessible so other developers or partners can use them. Finally, they can deploy the APIs in production using this functionality of Open Shift API management.
API analytics
As soon as it is in production, Open Shift API control allows to screen and offer insight into using the APIs. It will assist you in case your APIs are getting used, how they’re getting used, what demand looks like — and even whether the APIs are being abused. Understanding how your API is used is critical to help manipulate site visitors, anticipate provisioning wishes, and understand how your applications and APIs are used. Once more, all of this is right at your fingertips without having to commit employees to standing up or managing the provider and Amrita technologies will provide you all course details.
Single Sign-On -openshift
The addition of Red Hat SSO means organizations can choose to use their systems (custom coding required) or use Red Hat SSO, which is included with Open Shift API Management. (Please note that the SSO example is provided for API management only and is not a complete SSO solution.)Developers do not need administrative privileges. To personally access the API, it’s just there and there. Instead of placing an additional burden on developers, organizations can retain the user’s permissions and permissions.
Red Hat open shift container platform
These services integrate with Red Hat Open Shift Dedicated and Red Hat Open Shift platform Service for AWS, providing essential benefits to all teams deploying applications .The core services are managed by Red Hat, like Open Shift’s other managed services. This can help your organization reduce operating costs while accelerating the creation, deployment, and evaluation of cloud applications in an open hybrid cloud environment.
Streamlined developer experience in open shift
Developers can use the power and simplicity of three-tier API management across the platform. You can quickly develop APIs before serving them to internal and external clients and then publish them as part of your applications and services. It also provides all the features and benefits of using Kubernetes-based containers. Accelerate time to market with a ready-to-use development environment and help you achieve operational excellence through automated measurement and balancing rise.
Conclusion:
Redhat is a powerful solution that eases the management of APIs in environments running open shifts. Due to its integrability aspect, security concern, and developer-oriented features, it is an ideal solution to help firms achieve successful API management in a container-based environment.
0 notes
Text
Dominate NLP: Red Hat OpenShift & 5th Gen Intel Xeon Muscle

Using Red Hat OpenShift and 5th generation Intel Xeon Scalable Processors, Boost Your NLP Applications
Red Hat OpenShift AI
Her AI findings on OpenShift, where have been testing the new 5th generation Intel Xeon CPU, have really astonished us. Naturally, AI is a popular subject of discussion everywhere from the boardroom to the data center.
There is no doubt about the benefits: AI lowers expenses and increases corporate efficiency.
It facilitates the discovery of hitherto undiscovered insights in analytics and expands comprehension of business, enabling you to make more informed business choices more quickly than before.
Beyond only recognizing human voice for customer support, natural language processing (NLP) has become more valuable in business. These days, natural language processing (NLP) is utilized to improve machine translation, identify spam more accurately, enhance client Chatbot experiences, and even employ sentiment analysis to ascertain social media tone. It is expected to reach a worldwide market value of USD 80.68 billion by 2026 , and companies will need to support and grow with it quickly.
Her goal was to determine how Red Hat OpenShift‘s NLP AI workloads were affected by the newest 5th generation Intel Xeon Scalable processors.
The Support Red Hat OpenShift Provides for Your AI Foundation
Red Hat OpenShift is an application deployment, management, and scalability platform built on top of Kubernetes containerization technology. Applications become less dependent on one another as they transition to a containerized environment. This makes it possible for you to update and apply bug patches in addition to swiftly identifying, isolating, and resolving problems. In particular, for AI workloads like natural language processing, the containerized design lowers costs and saves time in maintaining the production environment. AI models may be designed, tested, and generated more quickly with the help of OpenShift’s supported environment. Red Hat OpenShift is the best option because of this.
The Intel AMX Modified the Rules
Intel released the Intel AMX, or fourth generation Intel Xeon Scalable CPU, almost a year ago. The CPU may optimize tasks related to deep learning and inferencing thanks to Intel AMX, an integrated accelerator.
The CPU can switch between AI workloads and ordinary computing tasks with ease thanks to Intel AMX compatibility. Significant performance gains were achieved with the introduction of Intel AMX on 4th generation Intel Xeon Scalable CPUs.
After Intel unveiled its 5th generation Intel Xeon Scalable CPU in December 2023, they set out to measure the extra value that this processor generation offers over its predecessor.
Because BERT-Large is widely utilized in many business NLP workloads, they explicitly picked it as deep learning model. With Red Hat OpenShift 4.13.2 for Inference, the graph below illustrates the performance gain of the 5th generation Intel Xeon 8568Y+ over the 4th generation Intel Xeon 8460+. The outcomes are Amazing
These Intel Xeon Scalable 5th generation processors improved its predecessors in an assortment of remarkable ways.
Performing on OpenShift upon a 5th generation Intel Xeon Platinum 8568the value of Y+ with INT8 produces up to 1.3x improved natural-language processing inference capability (BERT-Large) than previous versions with Inverse.
OpenShift on a 5th generation Intel Xeon Platinum 8568Y with BF16 yields 1.37x greater Natural Language Processing inference performance (BERT-Large) compared to previous generations with BF16.
OpenShift on a 5th generation Intel Xeon Platinum 8568Y+ with FP32 yields 1.49x greater Natural Language Processing inference performance (BERT-Large) compared to previous generations with FP32.
They evaluated power usage as well, and the new 5th Generation has far greater performance per watt.
Natural Language Processing inference performance (BERT-Large) running on OpenShift on a 5th generation Intel Xeon Platinum 8568Y+ with INT8 has up to 1.22x perf/watt gain compared to previous generation with INT8.
Natural Language Processing inference performance (BERT-Large) running on OpenShift on a 5th generation Intel Xeon Platinum 8568Y+ with BF16 is up to 1.28x faster per watt than on a previous generation of processors with BF16.
Natural Language Processing inference performance (BERT-Large) running on OpenShift on a 5th generation Intel Xeon Platinum 8568Y+ with FP32 is up to 1.39 times faster per watt than it was on a previous generation with FP32.
Methodology of Testing
Using an Intel-optimized TensorFlow framework and a pre-trained NLP model from Intel AI Reference Models, the workload executed a BERT Large Natural Language Processing (NLP) inference job. With Red Hat OpenShift 4.13.13, it evaluates throughput and compares Intel Xeon 4th and 5th generation processor performance using the Stanford Question Answering Dataset.
FAQS:
What is OpenShift and why it is used?
Developing, deploying, and managing container-based apps is made easier with OpenShift. Faster development and release life cycles are made possible by the self-service platform it offers you to build, edit, and launch apps as needed. Consider pictures as molds for cookies, and containers as the cookies themselves.
What strategy was Red Hat OpenShift designed for?
Red Hat OpenShift makes hybrid infrastructure deployment and maintenance easier while giving you the choice of fully managed or self-managed services that may operate on-premise, in the cloud, or in hybrid settings.
Read more on Govindhetch.com
0 notes
Text
Red Hat Named A Leader In Multicloud Container Platforms By Independent Research Firm

Red Hat, Inc., a prominent leader in open source solutions, has achieved a significant milestone by being recognized as a Leader in the Forrester Wave™ for Multicloud Container Platforms in the fourth quarter of 2023. Forrester Research, a reputable technology and market research firm, meticulously assessed and evaluated eight of the most influential providers in this domain, ranking them based on their current offerings, strategic vision, and market presence. In this rigorous evaluation, Red Hat emerged as a standout performer, earning the highest possible scores in an impressive 29 criteria.
One key aspect where Red Hat excelled in the Forrester evaluation was the developer experience. Red Hat OpenShift, the company's flagship multicloud container platform, received top marks for its user-friendly environment, making it an ideal choice for developers. The operator experience also received commendation, indicating that the platform is not only developer-friendly but also meets the operational needs of IT teams. This balance between developer and operator satisfaction is crucial in the world of container platforms.
DevOps automation, a critical requirement in modern software development, was another area where Red Hat stood out. The platform's automation capabilities streamline the development and deployment processes, facilitating faster and more efficient software delivery. This, in turn, contributes to better agility and competitiveness for organizations using Red Hat OpenShift.
Read More - https://bit.ly/3tkXlbF
0 notes